Exercise 1: Creating an HTTP Trojan and Remotely Controlling a Target Machine Using HTTP RAT
Remote access Trojans (RATs) provide attackers with full control over the victim’s system, enabling them to remotely access files, private conversations, and others. The RAT acts as a server and listens on a port that is not supposed to be available to Internet attackers. Therefore, if the user is behind a firewall on the network, there is less chance that a remote attacker would be able to connect to the Trojan. The attackers in the same network located behind the firewall can easily access Trojans.
Lab Scenario
HTTP/HTTPS Trojans can bypass any firewall, and work as kind of a straight HTTP tunnel, but one that works in reverse. They use web-based interfaces and port 80 to gain access. The execution of these Trojans takes place on the internal host and spawns a “child” at a predetermined time. The child program appears to be a user to the firewall so it allows the program access to the Internet. However, this child executes a local shell, connects to the web server that the attacker owns on the Internet through a legitimate-looking HTTP request, and sends it a ready signal. The legitimate-looking answer from the attacker’s web server is in reality a series of commands that the child can execute on the machine’s local shell.
Auditing a network against HTTP RATs is generally more difficult as well as essential, as most firewalls and other perimeter security devices cannot detect traffic generated by a HTTP RAT Trojan. As an ethical hacker and pen-tester, you must understand the working of HTTP Trojans to protect your networks against such malware.
Auditing a network against HTTP RATs is generally more difficult as well as essential, as most firewalls and other perimeter security devices cannot detect traffic generated by a HTTP RAT Trojan. As an ethical hacker and pen-tester, you must understand the working of HTTP Trojans to protect your networks against such malware.
Lab Objectives
In this lab, you will learn how to:
- Run HTTP Trojan on Windows Server 2012 and create a Server
- Execute the Server from Windows 10 Machine
- Control Windows 10 machine Remotely from Windows Server 2012
Lab Duration: 5 Minutes
- By default, Windows Server 2016 machine is selected click Ctrl+Alt+Delete.
Alternatively navigate to Commands (Thunder icon) menu and click Ctrl+Alt+Delete.
- In the Password field click Pa$$w0rd and press Enter to login.
Alternatively navigate to Commands (Thunder icon) menu Type Text and click Type Password.
- To launch HTTP RAT, navigate to E:\CEHv10 Module 07 Malware Threats\Trojans Types\HTTP HTTPS Trojans\HTTP RAT TROJAN and double-click httprat.exe.
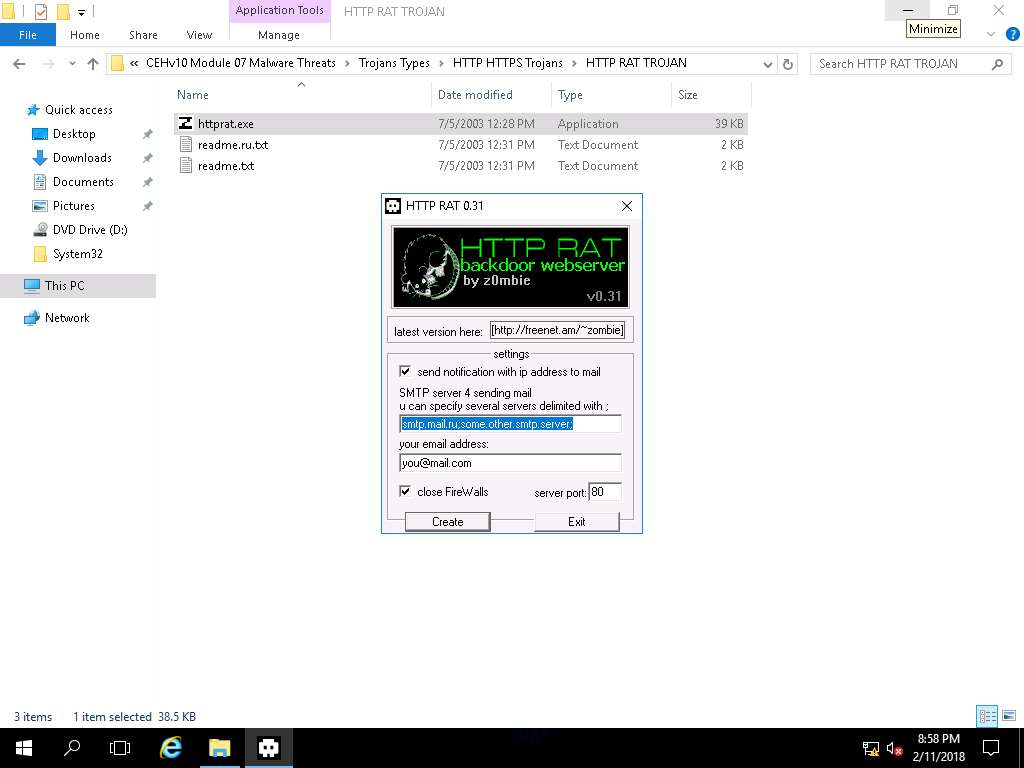
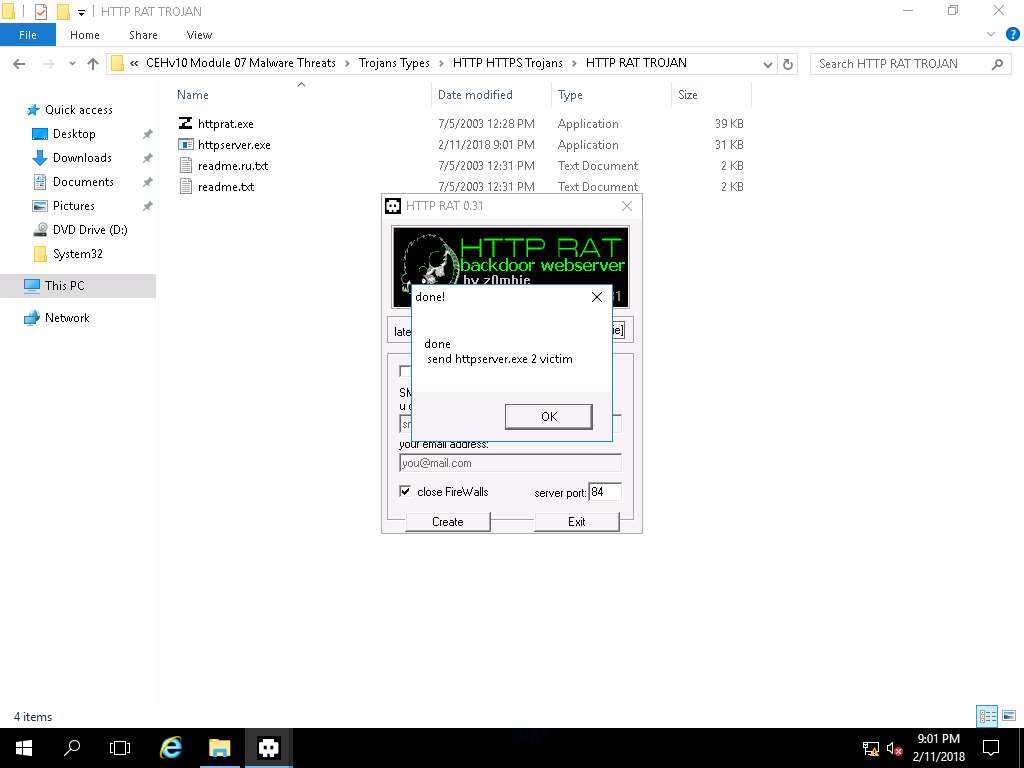
- HTTP RAT main window appears as shown in the screenshot. Uncheck send notification with ip address to mail option, enter server port 84, and click Create to create a httpserver.exe file.
- The server will be created in the default location where HTTP RAT files are available. In this lab the server is created in the following location E:\CEHv10 Module 07 Malware Threats\Trojans Types\HTTP HTTPS Trojans\HTTP RAT TROJAN.
Minimize all the windows that were opened.
- Click Windows 8, and click Ctrl+Alt+Delete.
Alternatively navigate to Commands (Thunder icon) menu and click Ctrl+Alt+Delete.

- In the Password field click Pa$$w0rd and press Enter to login.
Alternatively navigate to Commands (Thunder icon) menu Type Text and click Type Password.
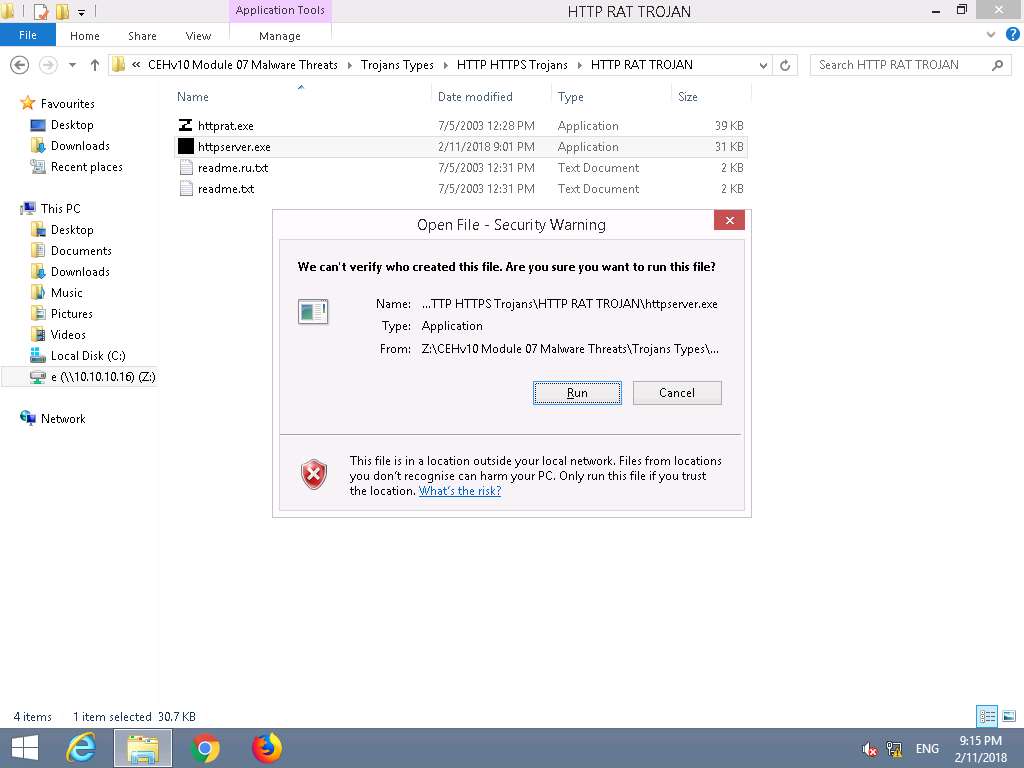
- To run httpserver.exe navigate to Z:\CEHv10 Module 07 Malware Threats\Trojans Types\HTTP HTTPS Trojans\HTTP RAT TROJAN and double-click httpserver.exe.
Open File - Security Warning window appears, click Run.
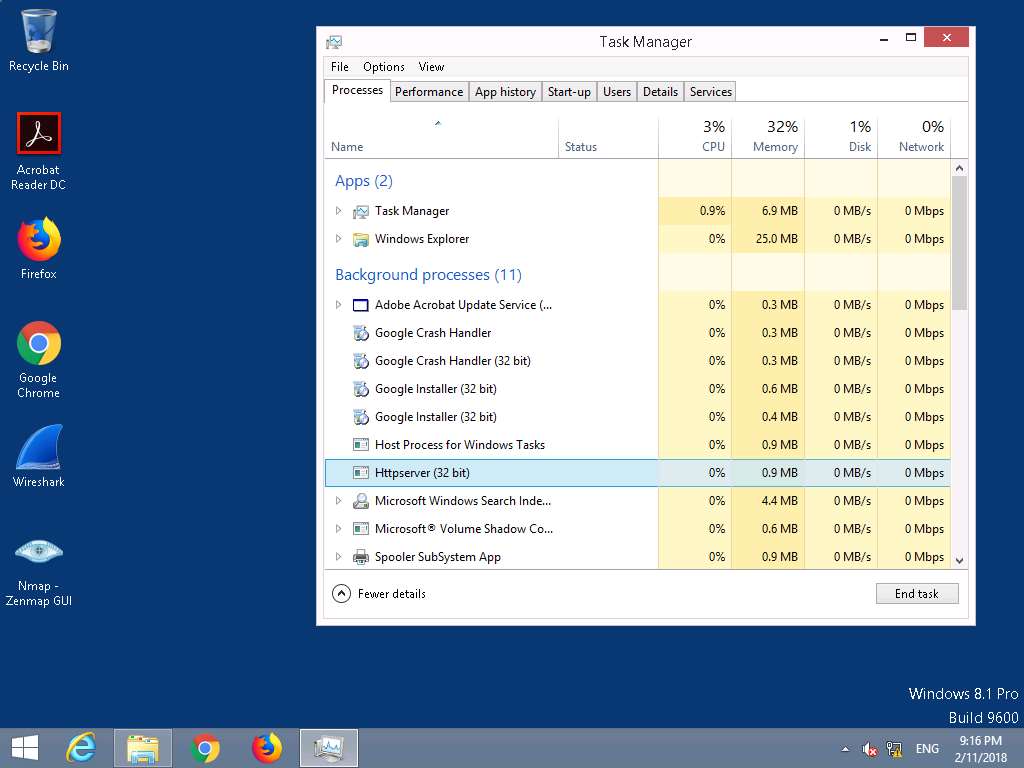
- The httpserver.exe runs in the background, to confirm the status open the Task Manager. In the Processes tab you will find Httpserver (32bit) running. Leave the Windows 8 machine running.
- Click Windows Server 2016.
- Launch any browser (here, Google Chrome). Double-click shortcut icon of the any browser to launch. In this lab we are using Google Chrome.
- In the address bar of the browser type the IP address of the victim machine and press Enter. Here Windows 8 is the victim machine and its IP address is 10.10.10.8.
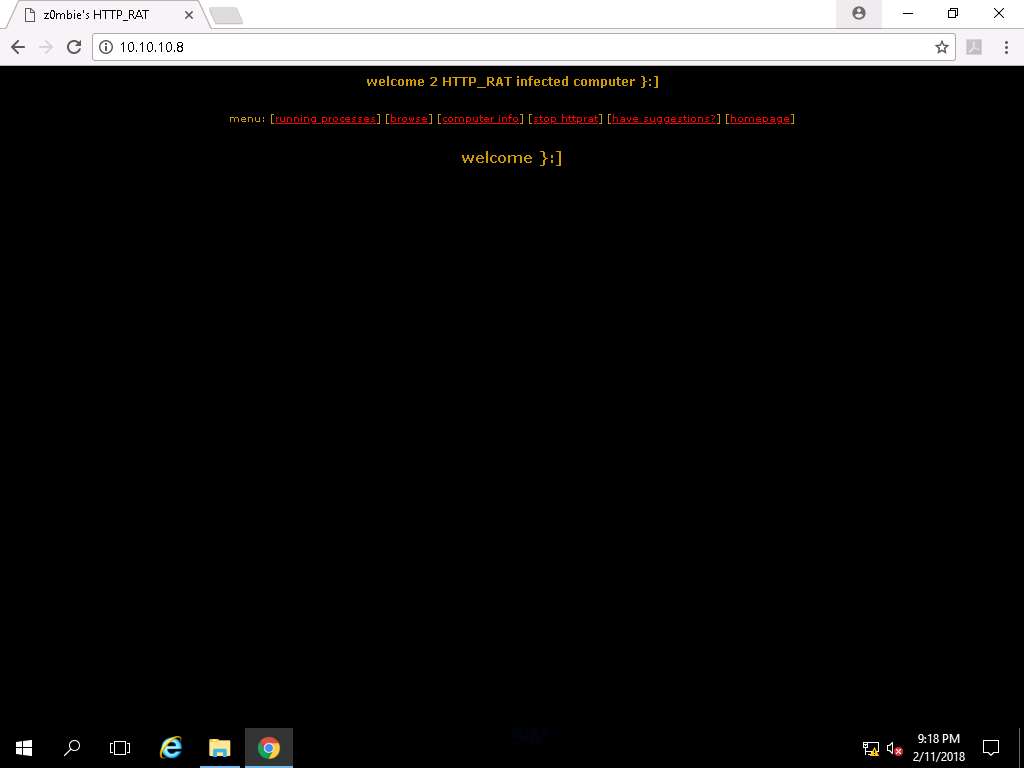
- z0mbie's HTTP_RAT Page appears as shown in the screenshot. Click on the running processes link to list down the processes running on the Windows 8 machine.
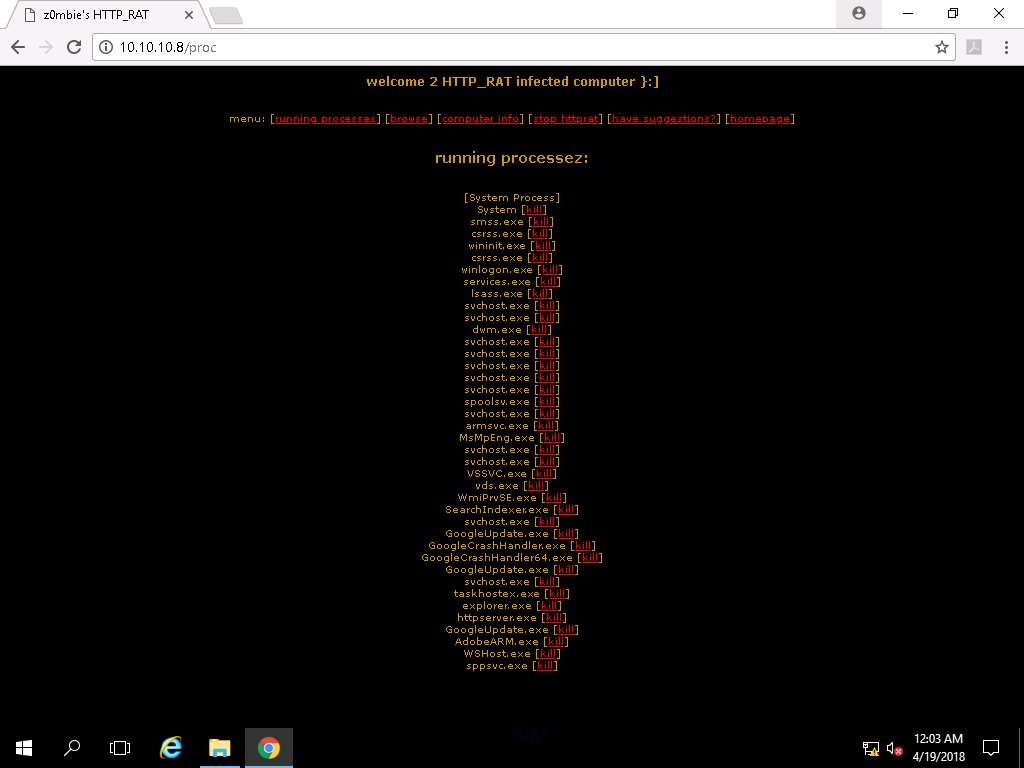
- Running Processes list appears that are running in the victim machine as shown in the screenshot. You can kill any running process from here.
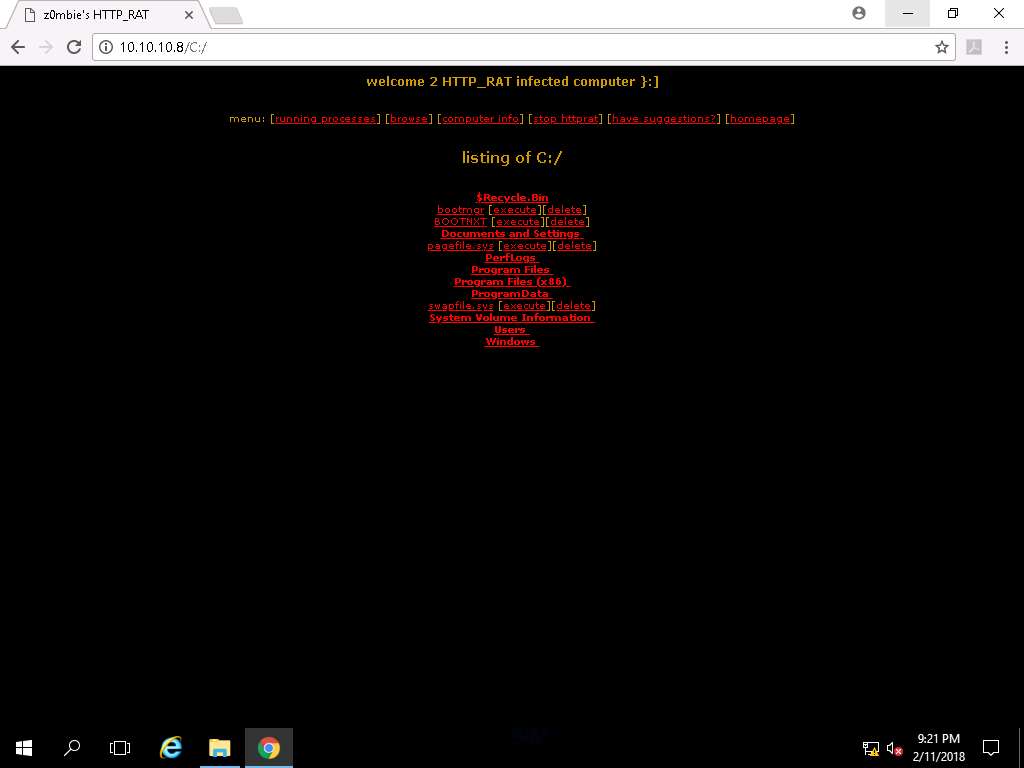
- Click browse, to browse the directories and files in the victim machine.. Once you click browse link, it will display the available list of the drives in the victim machine. You can browse the contents any drive by clicking on the respective links.
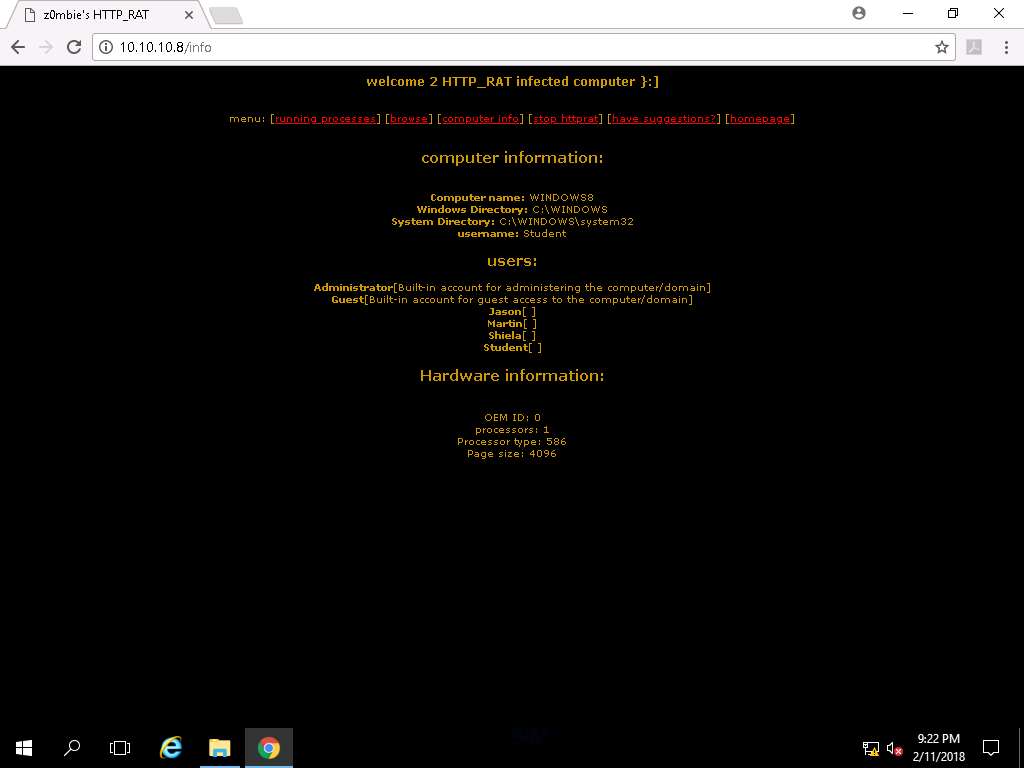
- Click computer info link to view the information of the computer, users, and hardware.
In real time, attackers run this tool in the target machine, create a server in that machine, and execute it. By doing so, they obtain data contained in that machine as well as the information related to its hardware and software.
On completion of the lab, end the Httpserver process in Windows 8.
- On completion of the lab, close all the windows.
In this lab, you have learnt how to:
- Run HTTP Trojan on Windows Server 2012 and create a Server
- Execute the Server from Windows 10 Machine
- Control Windows 10 machine Remotely from Windows Server 2012
