Exercise 5: Creating a Server Using the ProRat Tool
ProRat is a Remote Administration Tool written in C programming language and capable of working with all Windows operating systems.
Lab Scenario
Attackers use malware to steal personal information, financial data, and business information from target systems. ProRat is a “remote administration tool” made by PRO Group. ProRat was written in C programming language and capable of working with all Windows operating systems. ProRat was designed to allow users to control their own computers remotely from other computers. However, attackers have co-opted it for their own nefarious purposes. Some hackers take control of remote computer systems to conduct a denial of service (DoS) attack, which renders the target system unavailable for normal personal or business use. These targeted systems have included high-profile web servers such as banks and credit card gateways.
You, as an ethical hacker or pen-tester, can use ProRat to audit your own network against remote access Trojans.
You, as an ethical hacker or pen-tester, can use ProRat to audit your own network against remote access Trojans.
Lab Objectives
The objective of this lab is to help students learn to detect Trojan and backdoor attacks.
The objectives of this lab include:
The objectives of this lab include:
- Creating a server and testing the network for attack
- Attacking a network using sample Trojans and documenting all vulnerabilities and flaws detected
Lab Duration: 10 Minutes
- Click Windows 10, and then click Ctrl+Alt+Delete.
Alternatively click Ctrl+Alt+Delete from Commands menu (Thunder icon).
- In the Password field click Pa$$w0rd and press Enter to login.
Alternatively navigate to Commands (Thunder icon) menu Type Text and click Type Password.
- To launch ProRAT, navigate to Z:\CEHv10 Module 07 Malware Threats\Trojans Types\Remote Access Trojans (RAT)\ProRat and double-click on ProRat.exe.
If an Open File - Security Warning pop-up appears, click Run.
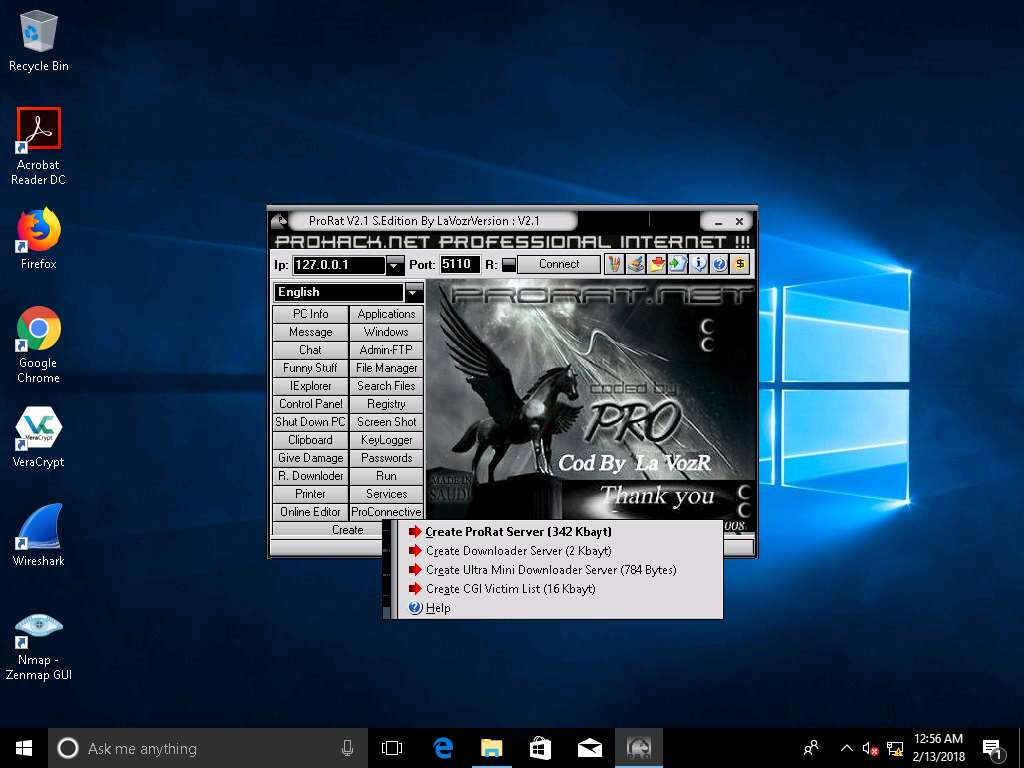
- ProRat main window appears, click Create. Click Create ProRat Server (342 Kbayt) to create a ProRat server.
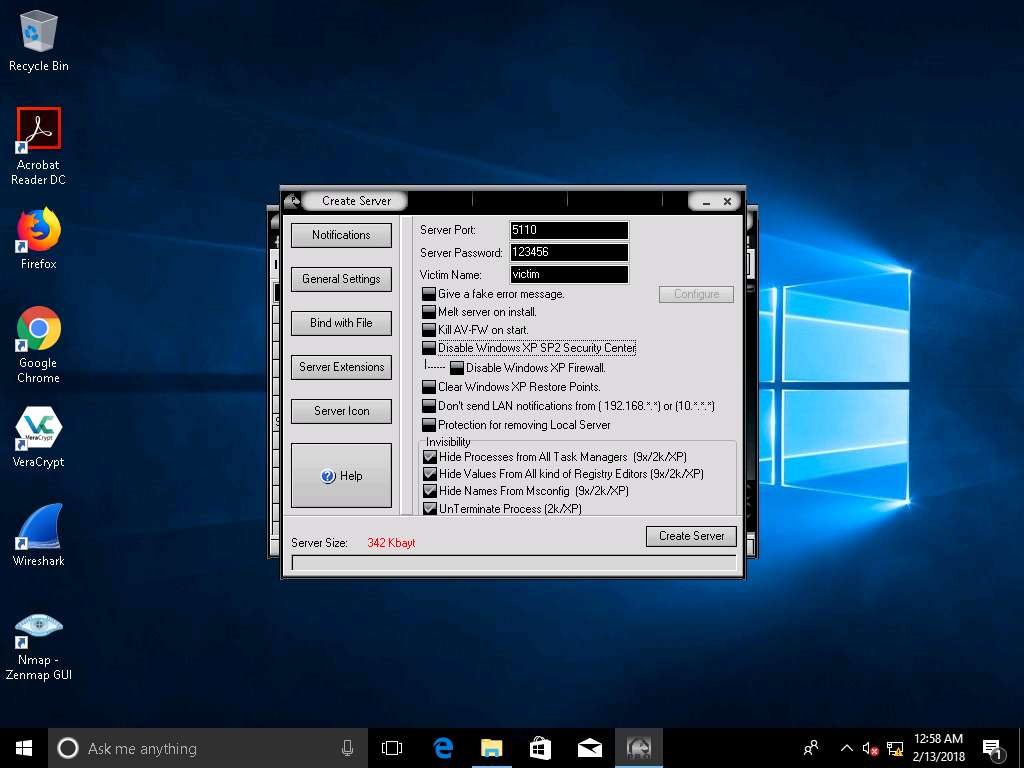
- Create Server window appears. In Notifications leave the settings to default.
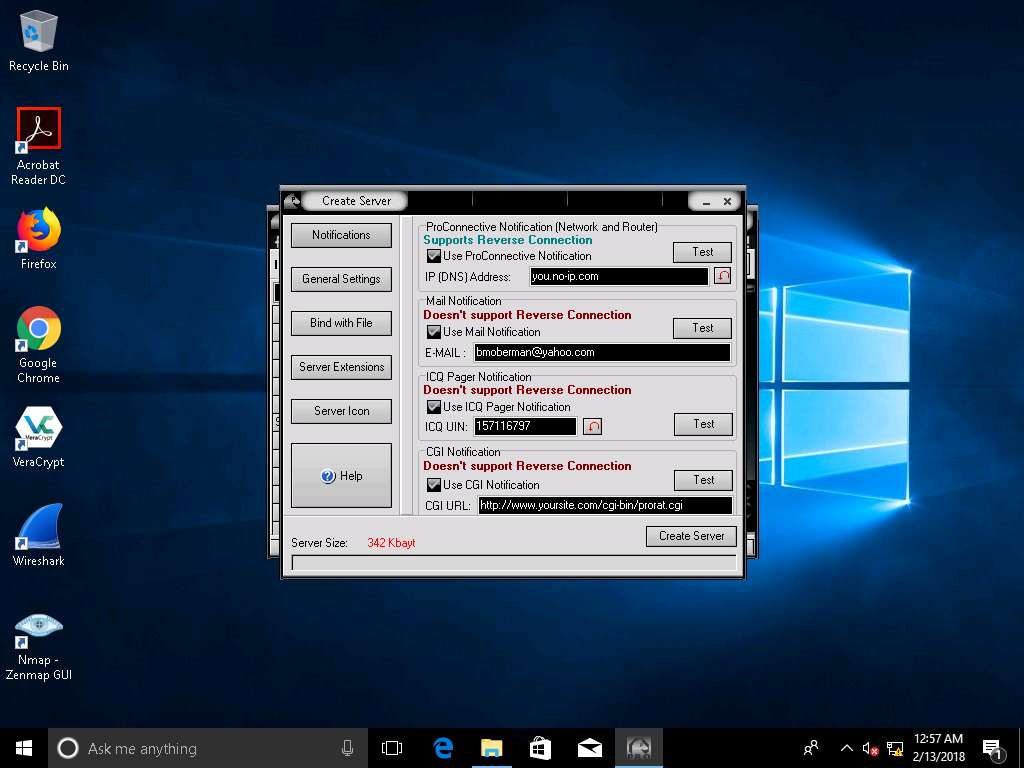
- Click on General Settings button to configure features such as Server Port, Server Password, Victim Name, and the port number. In this lab, default settings are chosen. Note down the Server password.
Uncheck the options, as shown in the screenshot.
- Click Bind with file button to bind sever with a file. In this lab, we are using .jpg file to bind the server. Check Bind server with a file option, click Select File button, and navigate to Z:\CEHv10 Module 07 Malware Threats\Trojans Types\Remote Access Trojans (RAT)\ProRat\Images.
Select MyCar.jpg in browse window, and click Open to bind the file.
- A pop-up displays the prompt: ProRat server will bind with MyCar.jpg. Click OK.
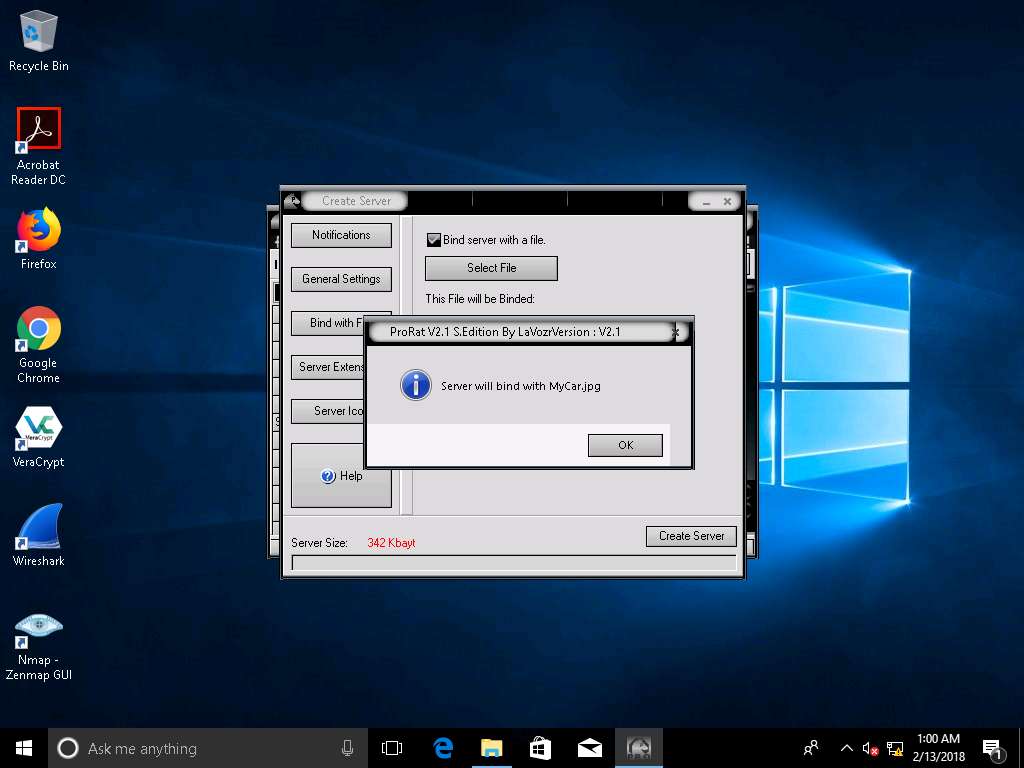
- Click Server Extensions. Under Select Server Extension, check EXE (Has icon support).
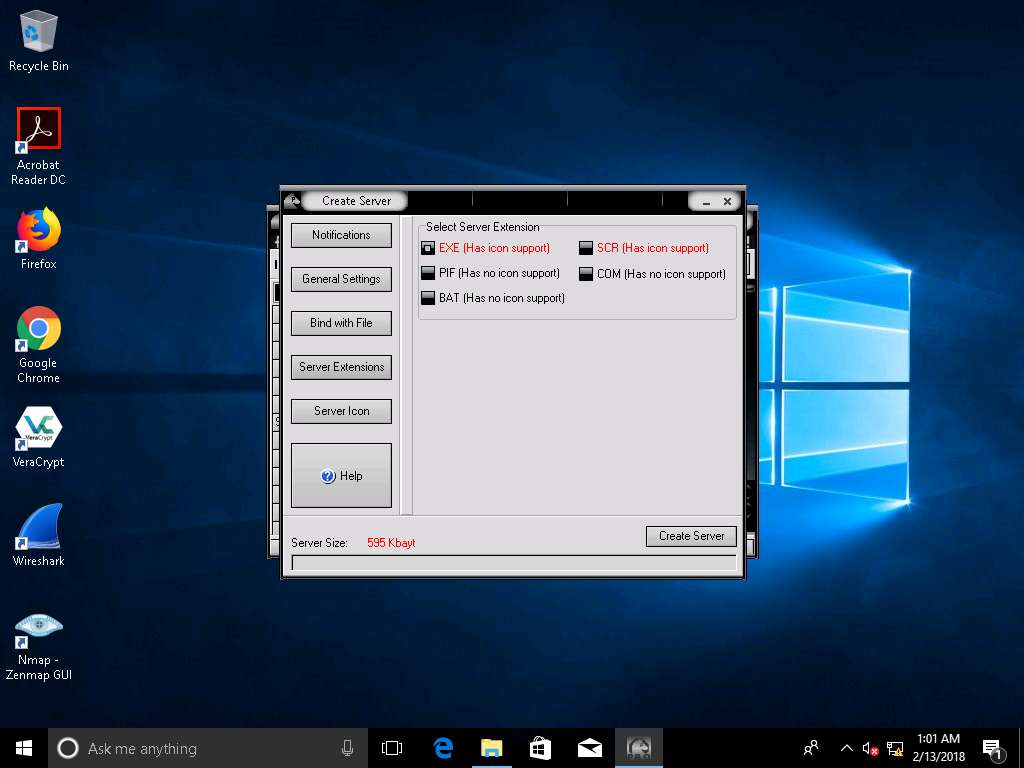
- Click Server Icon. Under Server Icon, select any icon, and click Create Server.
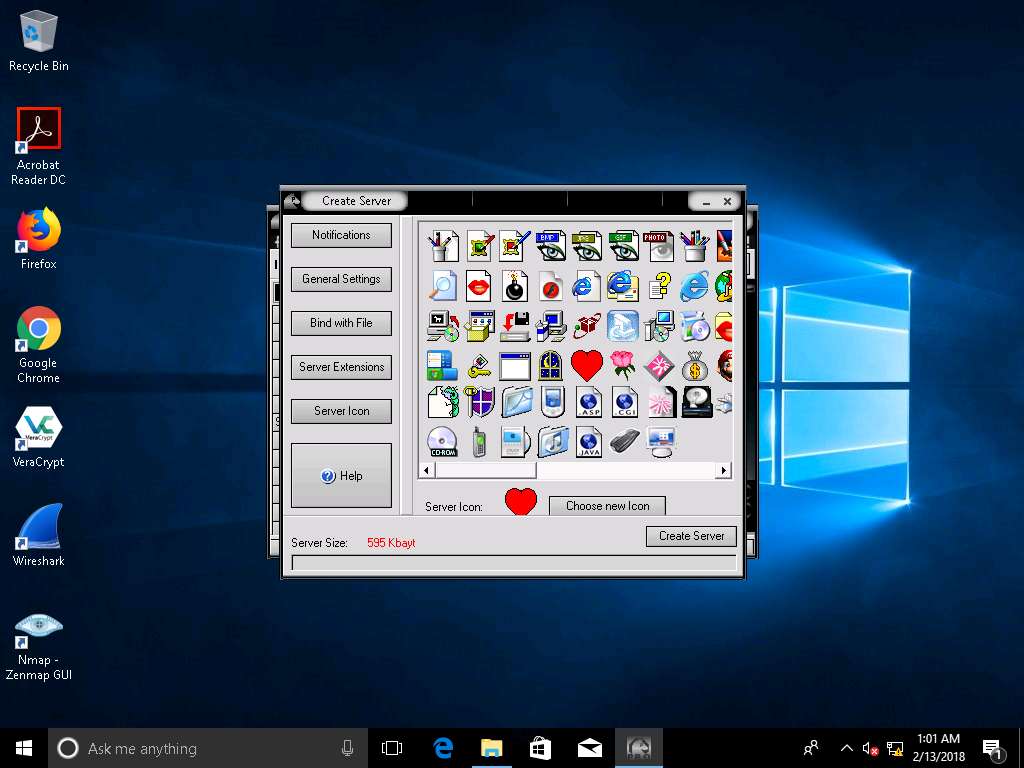
- A pop-up states that the server has been created. Click OK.
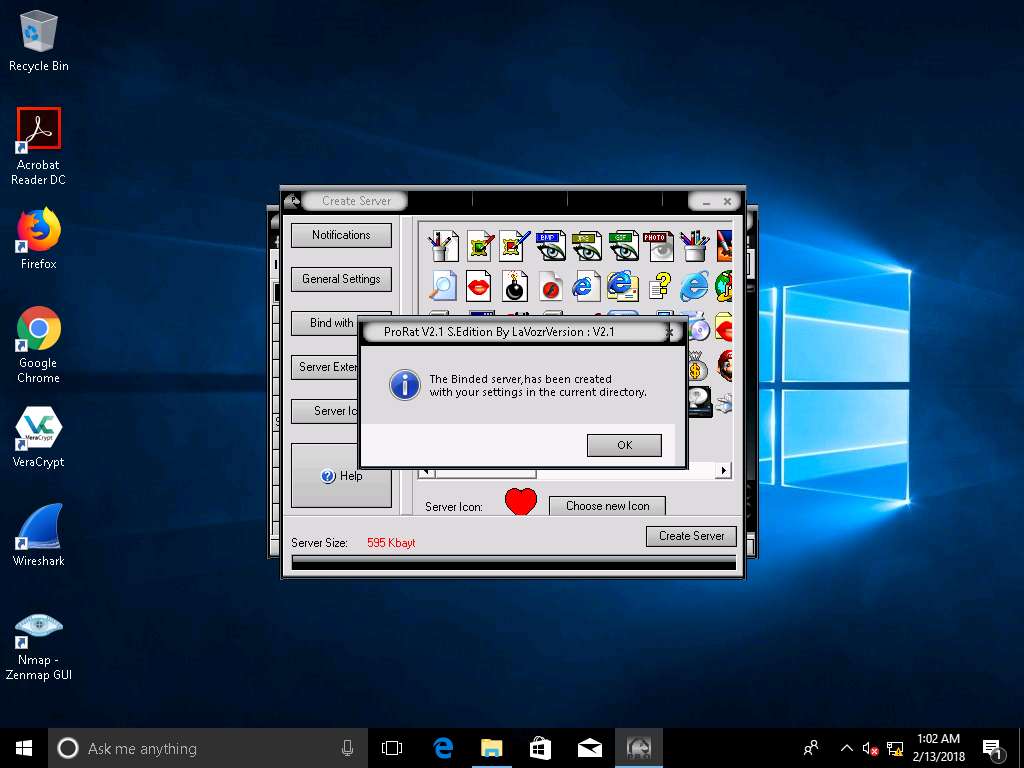
- The created server will be saved in Z:\CEHv10 Module 07 Malware Threats\Trojans Types\Remote Access Trojans (RAT)\ProRat. This server is named binded_server by default. Close the Create Server window of the ProRat.
In real time, hackers may craft such servers and send them by mail or any communication media to the victim’s machine.
You need to zip the file before mailing it, as you cannot attach .exe files on some mail servers.
- Click Windows Server 2012, and then click Ctrl+Alt+Delete.
Alternatively click Ctrl+Alt+Delete from Commands menu (Thunder icon).
- In the Password field click Pa$$w0rd and press Enter to login.
Alternatively navigate to Commands (Thunder icon) menu Type Text and click Type Password.
- To execute the Trojan, navigate to Z:\CEHv10 Module 07 Malware Threats\Trojans Types\Remote Access Trojans (RAT)\ProRat, and double-click binder_server.exe.
If the Open File - Security Warning pop-up appears, click Run. Leave the Windows Server 2012 machine running.
- Click Windows 10, and enter the IP address of Windows Server 2012; keep the default port number in the ProRat main window, and click Connect.
In this lab IP address of the Windows Server 2012 is 10.10.10.12.
- Enter the password you noted down at the time of creating Server and click OK.
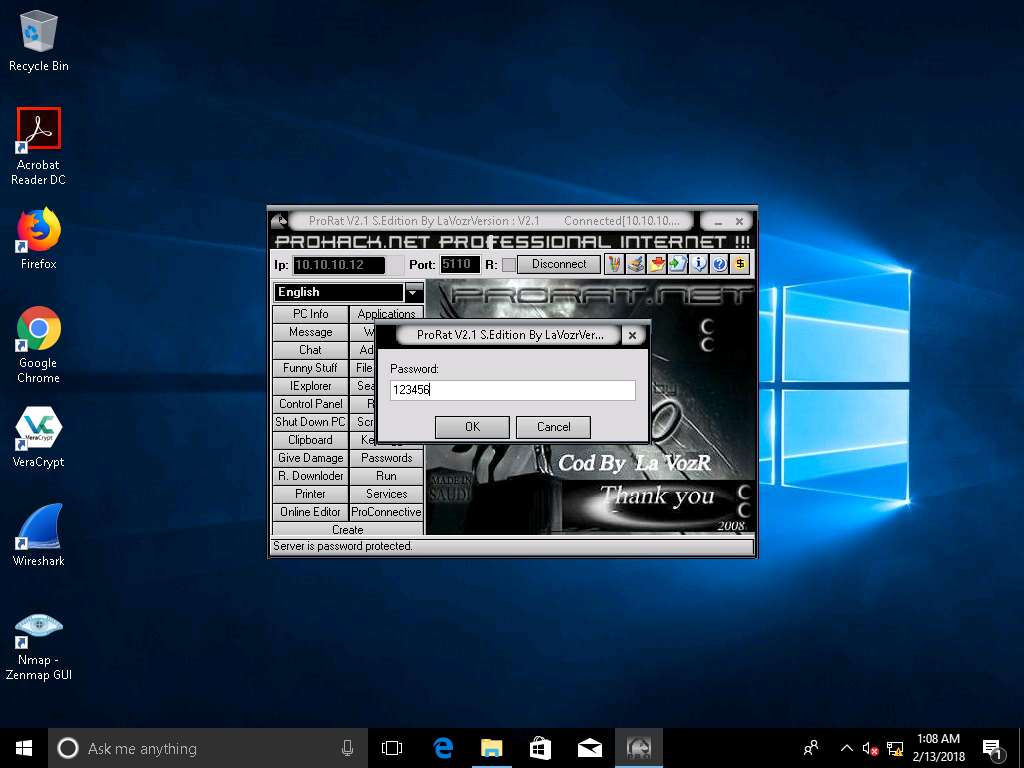
- Now you are connected to the victim machine. ProRat begins to monitor the user activities. It records all passwords, keystrokes, and so on.
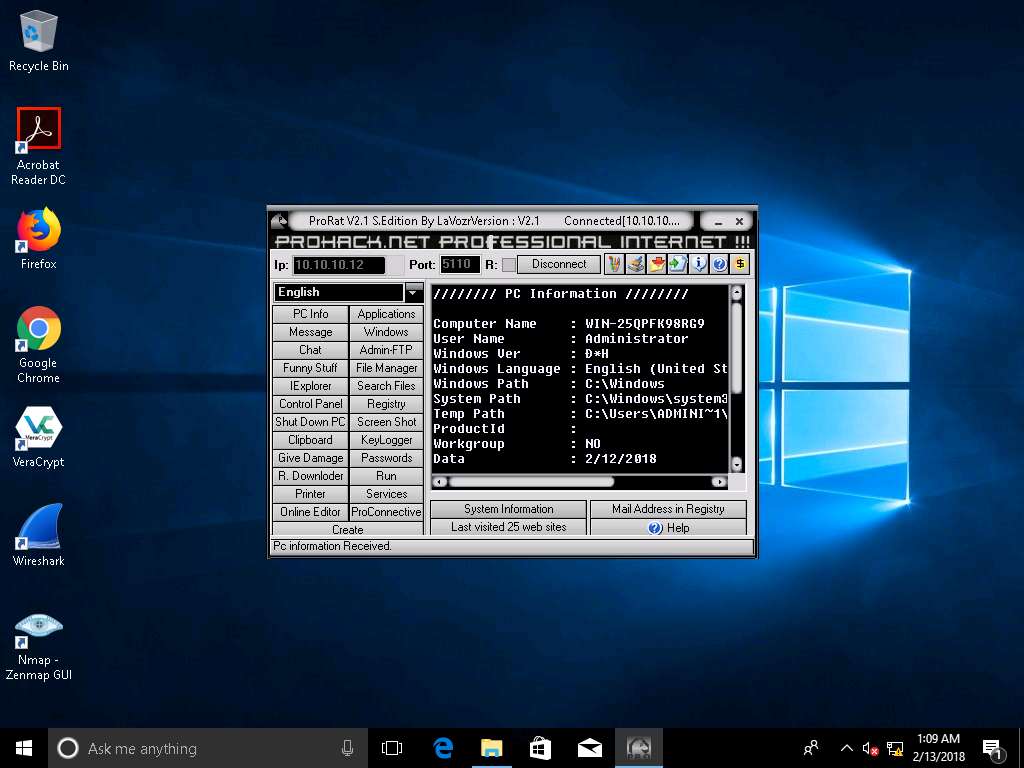
To test the connection, click PC Info, and choose System Information. ProRat displays the information of the victim machine, as shown in the screenshot.
- Click on Keylogger to steal user passwords for the online system. KeyLogger window appears, leave the Keylogger window running.
- Click Windows Server 2012, or Notepad, and type any text, as shown in the screenshot.
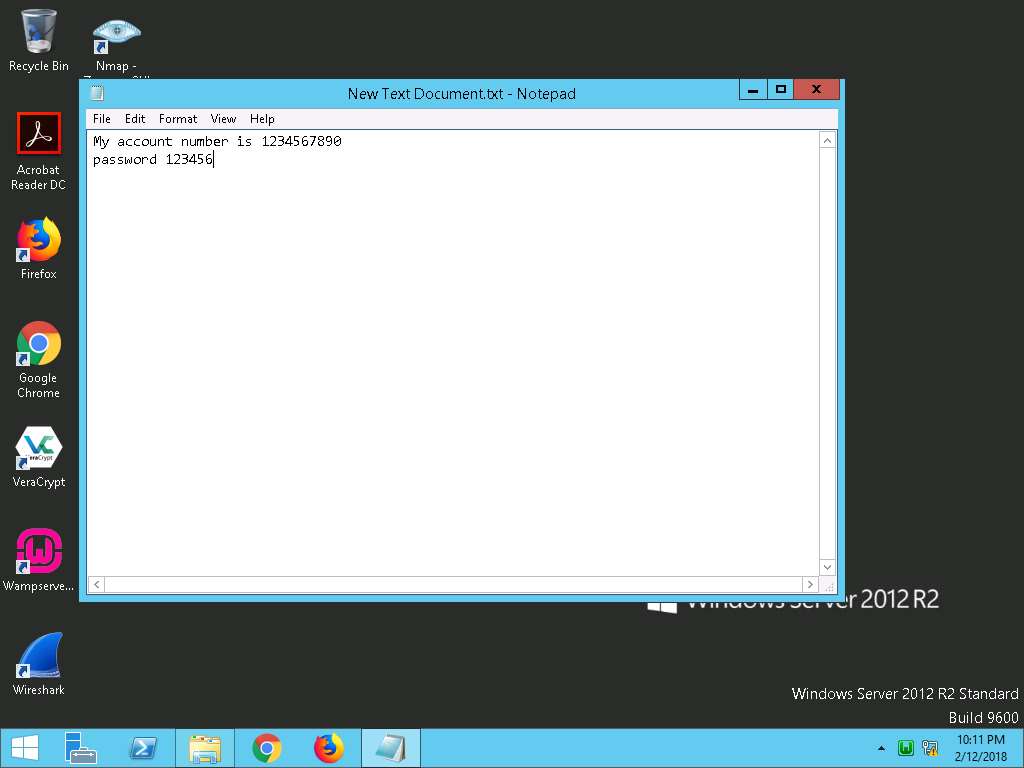
- Click Windows 10 machine, click Read Log button in the Keylogger window. To record the keystrokes of the victim machine. Close the keylogger window.
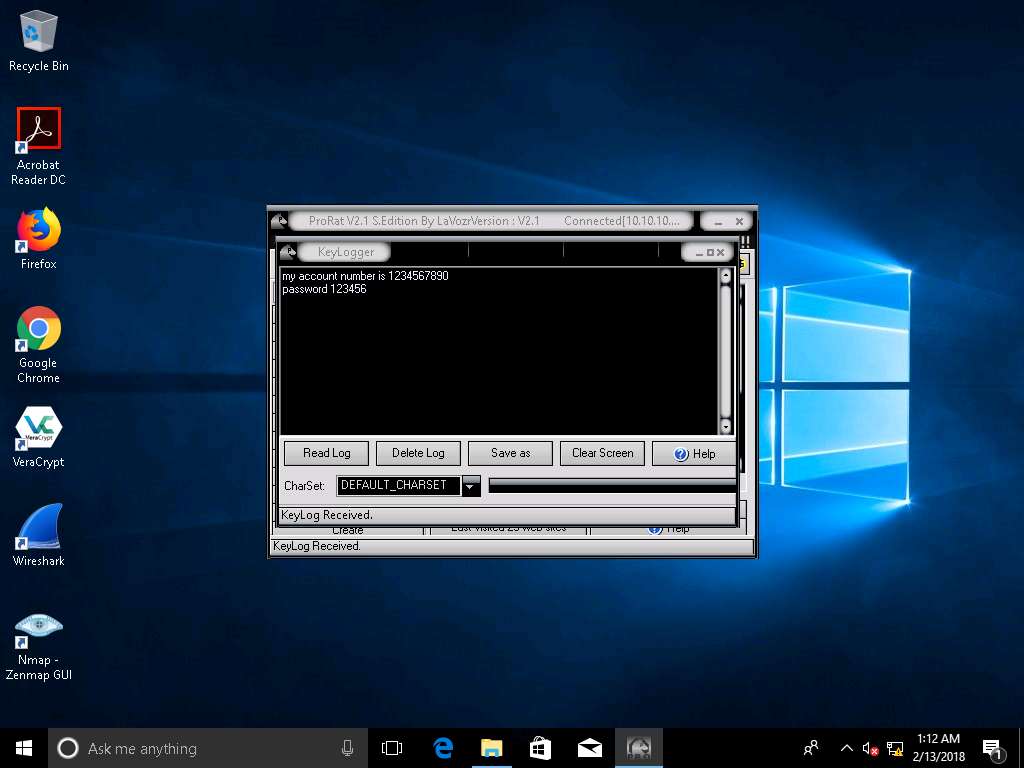
- Now click the Registry button to view registry editor of the Windows Server 2012 machine.
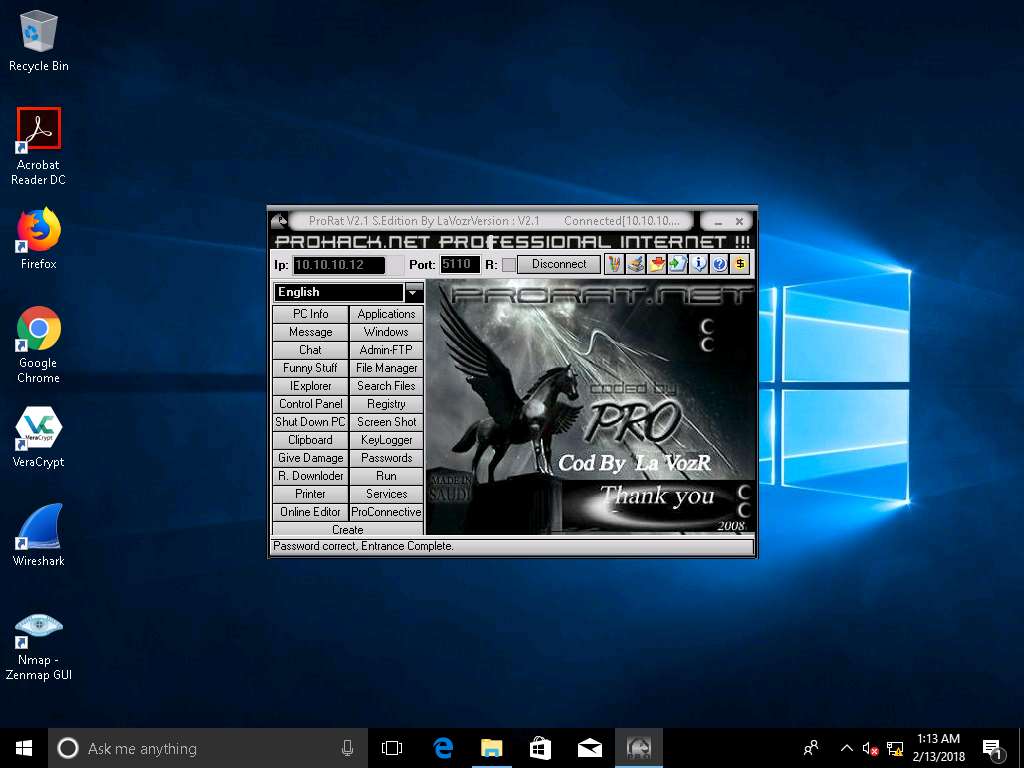
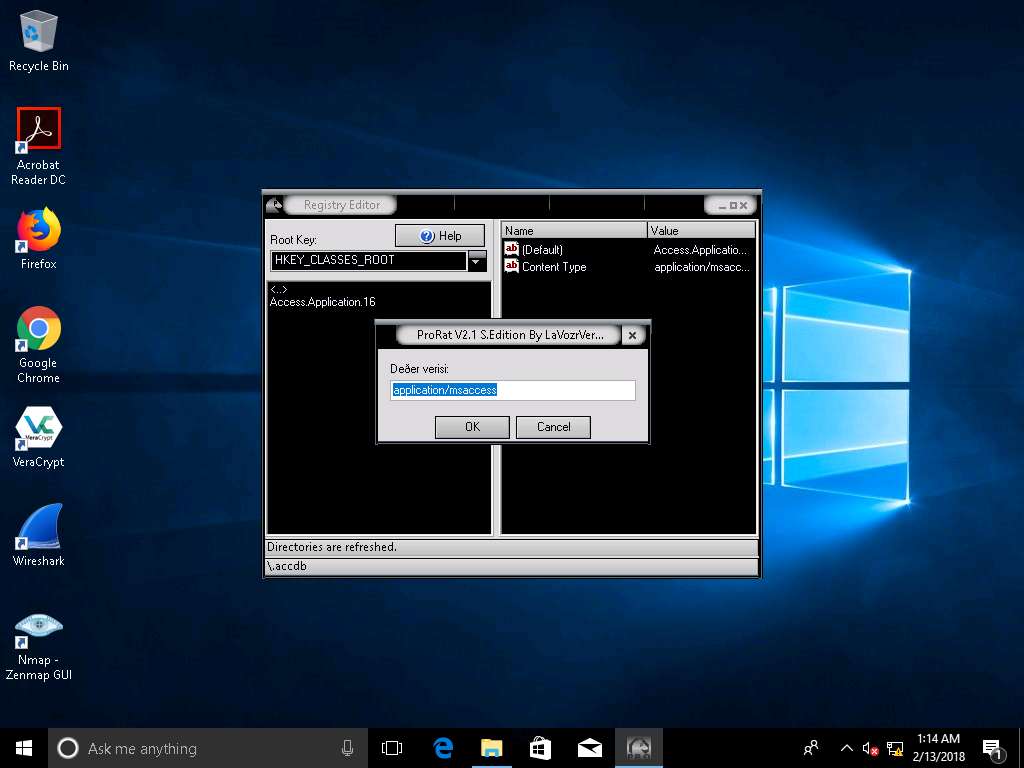
- Registry Editor window appears, where you can choose the Registry Editor from the Root Key: drop-down list and you can see and also modify the registry of the victim’s machine as shown in the screenshot.
Close the Registry related windows, and switch back to the main window of the ProRat. In the same way, you can make use of the other options that allow you to explore and control the victim machine.
- On completion of the lab, close all the windows.
In this lab you have learnt how to:
- Creating a server and testing the network for attack
- Attacking a network using sample Trojans and documenting all vulnerabilities and flaws detected
