Exercise 2: Creating a Trojan Server Using the GUI Trojan MoSucker
MoSucker is a Visual Basic Trojan. MoSucker's edit server program lets the infection routine be changed and notification information set. MoSucker can auto load with the system.ini and/or the registry. Unlike any other Trojan, MoSucker can be set to randomly choose which method to auto load. It can notify cell phones via SMS in Germany only. MuSucker’s edit server can gain X number of kilobytes (X is either a static number or it is random each time). The standard error message for MoSucker is "Zip file is damaged, truncated, or has been changed since it was created. If you downloaded this file, try downloading again.” Here is a list of file names MoSucker suggests to name the server: MSNETCFG.exe, unin0686.exe, CaIc.exe, HTTP.exe, MSWINUPD.exe, Ars.exe, NETUPDATE.exe, and Register.exe.
Server Features:
- Chat with victim
- Clipboard manager
- Close/remove server
- Control mouse
- Crash System File Manager
- Get passwords entered by user, system info
- Hide/Show start button, system tray, taskbar
- Keylogger
- Minimize all windows
- Open/close CD-ROM drive
- Ping server
- Pop-up startmenu
- Process manger
- Shutdown/Reboot/Standby/Logoff/Dos mode server
- System keys on/off
- Window manager
Lab Scenario
MoSucker is a backdoor Trojan written in Visual Basic, affecting most of the versions of Windows operating systems. The backdoor uses a client/server relationship, in which the installation of server component takes place in the victim's system, and the remote attacker has control of the client.
You are a Security Administrator of your company, and your job responsibilities include protecting the network from malware, Trojan attacks, theft of valuable network data, and identity theft.
You are a Security Administrator of your company, and your job responsibilities include protecting the network from malware, Trojan attacks, theft of valuable network data, and identity theft.
Lab Objectives
The objective of this lab is to help students learn to detect Trojan and backdoor attacks.
The objectives of the lab include:
The objective of this lab is to help students learn to detect Trojan and backdoor attacks.
The objectives of the lab include:
- Creating a server and testing the network for attack
- Access the victim machine remotely
Lab Duration: 5 Minutes
- Click Windows Server 2012, and click Ctrl+Alt+Delete.
Alternatively navigate to Commands (Thunder icon) menu and click Ctrl+Alt+Delete.
- In the Password field click Pa$$w0rd and press Enter to login.
Alternatively navigate to Commands (Thunder icon) menu Type Text and click Type Password.
- To create a server, navigate to Z:\CEHv10 Module 07 Malware Threats\Trojans Types\Remote Access Trojans (RAT)\MoSucker. Double-click CreateServer.exe file to create a server.
If an Open File - Security Warning pop-up appears, click Run.
If the VB6 Runtimes pop-up appears, click OK.
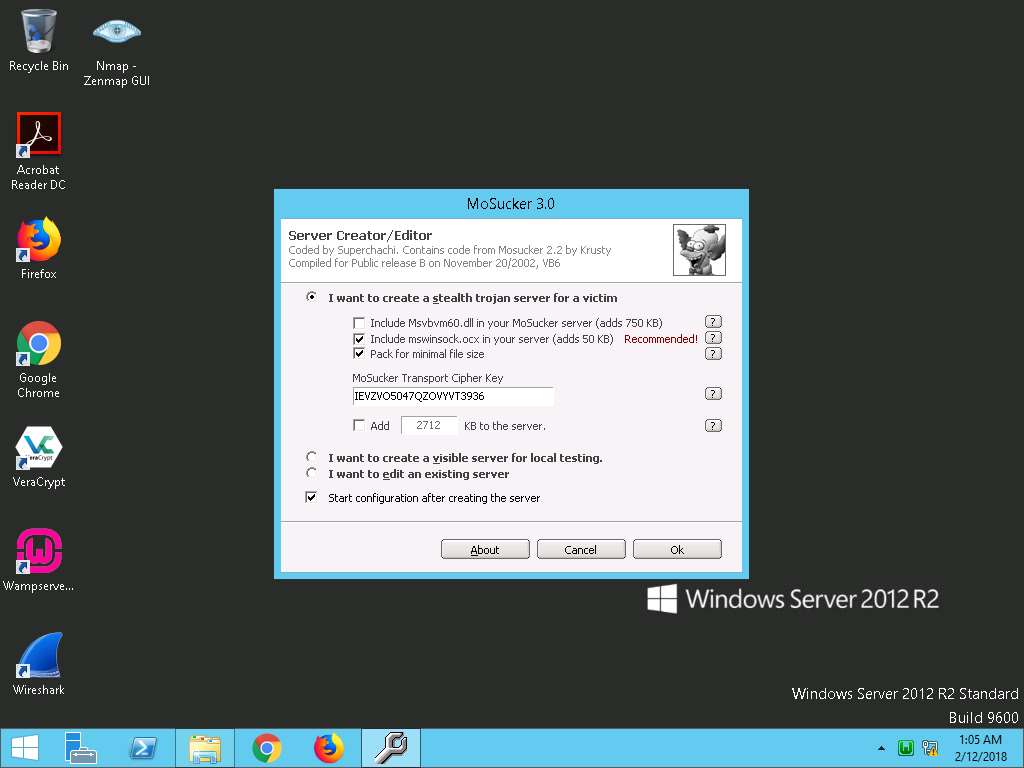
- The MoSucker Server Creator/Editor window appears; leave the default settings, and click OK.
- Choose a location (Z:\CEHv10 Module 07 Malware Threats\Trojans Types\Remote Access Trojans (RAT)\MoSucker) to save the file, specify a file name (server.exe), and click Save.
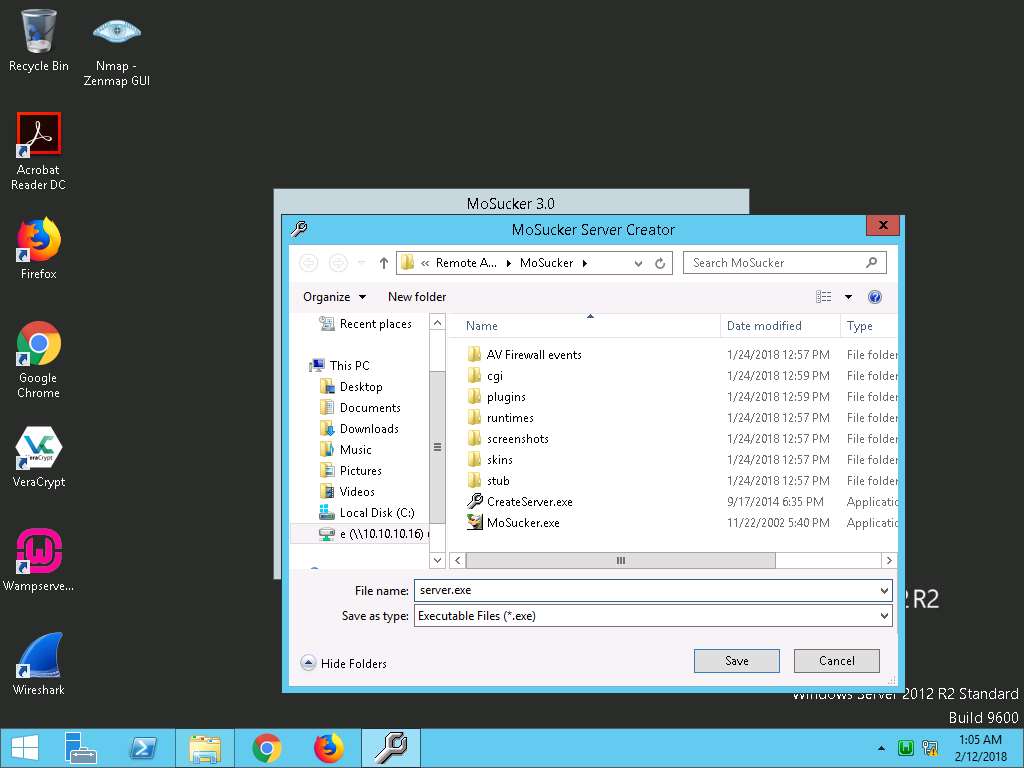
- Once the server is created, an Edit Server pop-up appears; click OK.
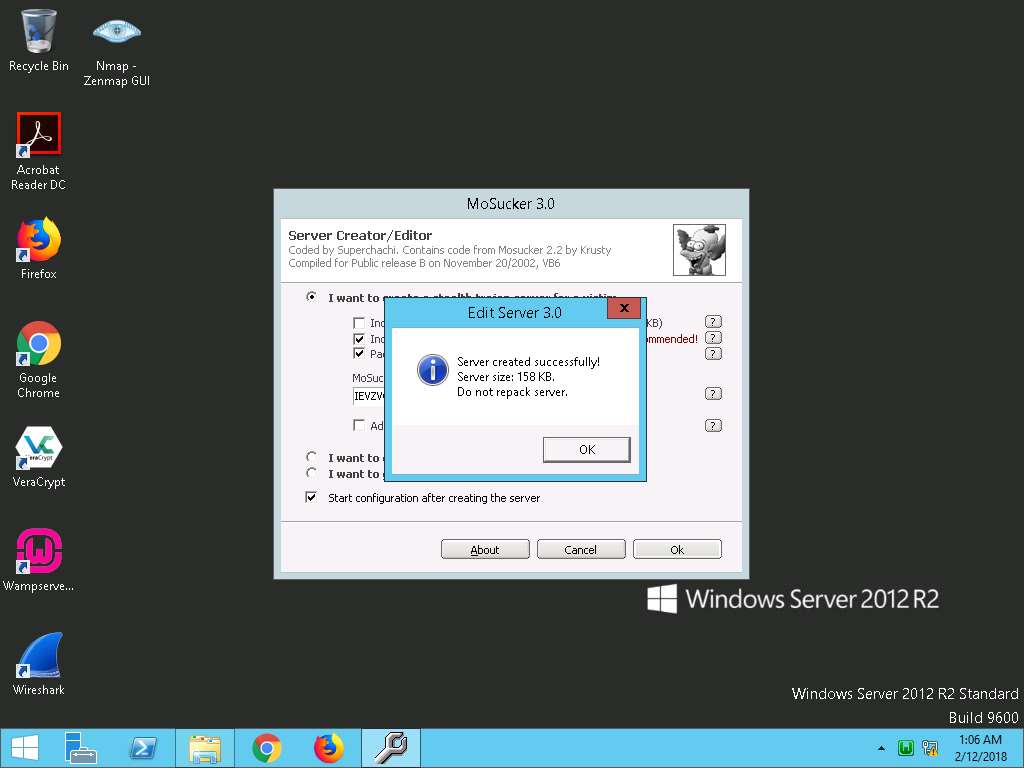
- In MoSucker wizard, change Victim’s Name, or leave all the settings to default. Make a note of the Connection-port number (here, 4288).
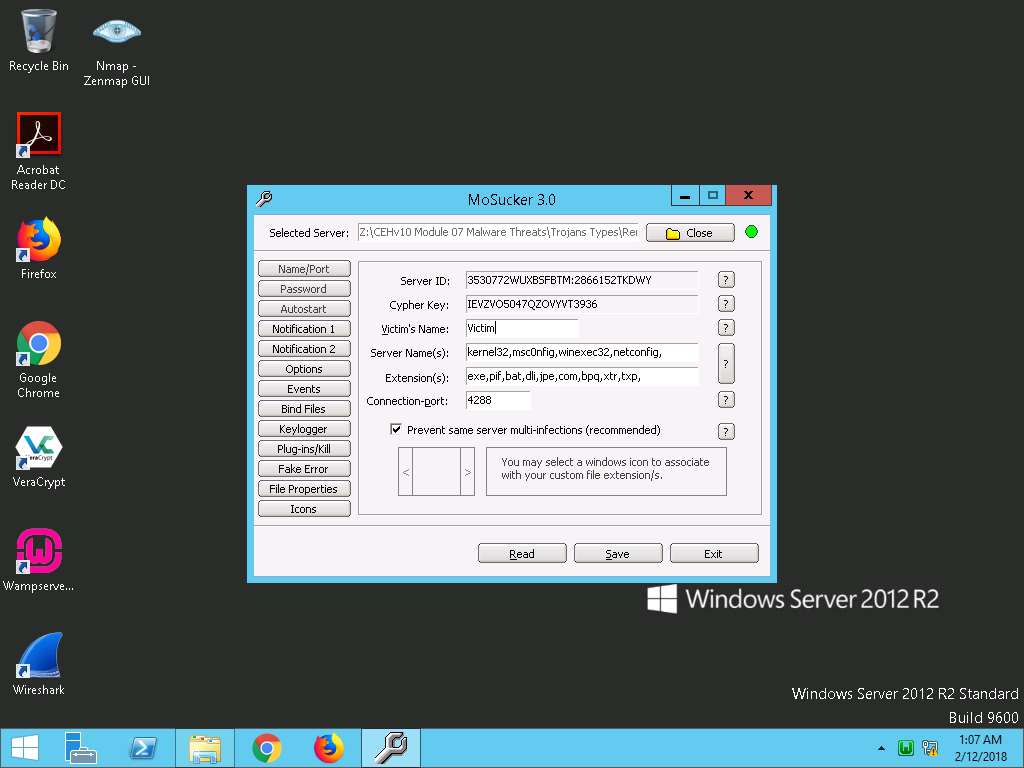
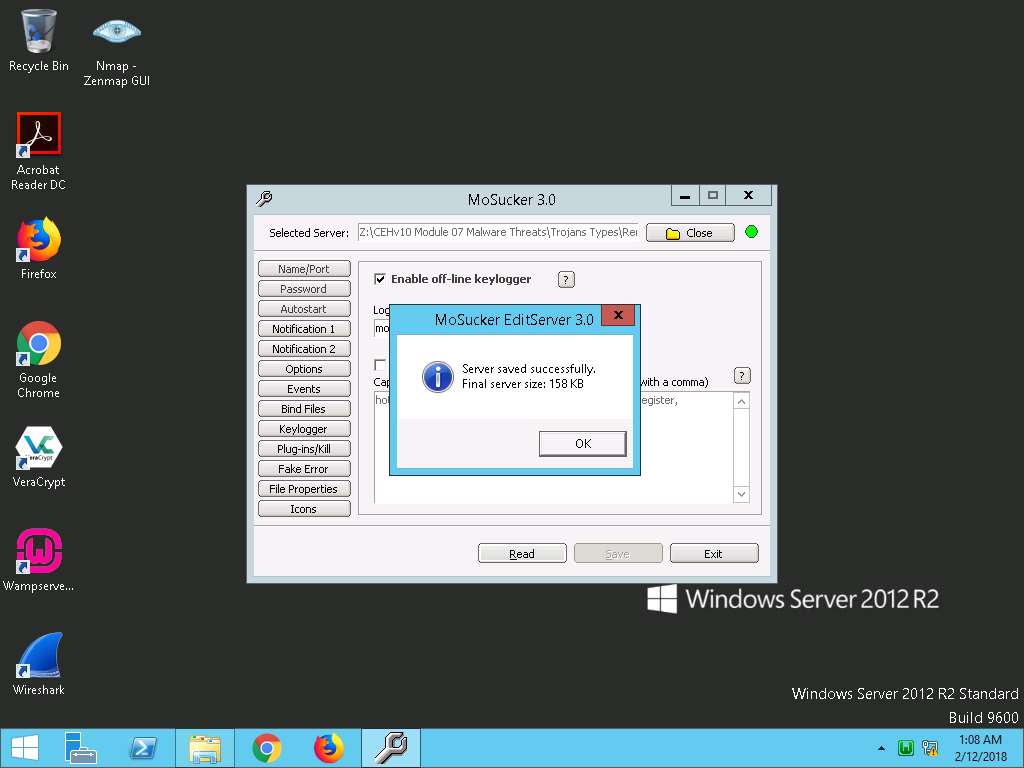
- Now, select Keylogger button in the left pane, check Enable off-line keylogger, and leave the other settings at their defaults. Click Save.
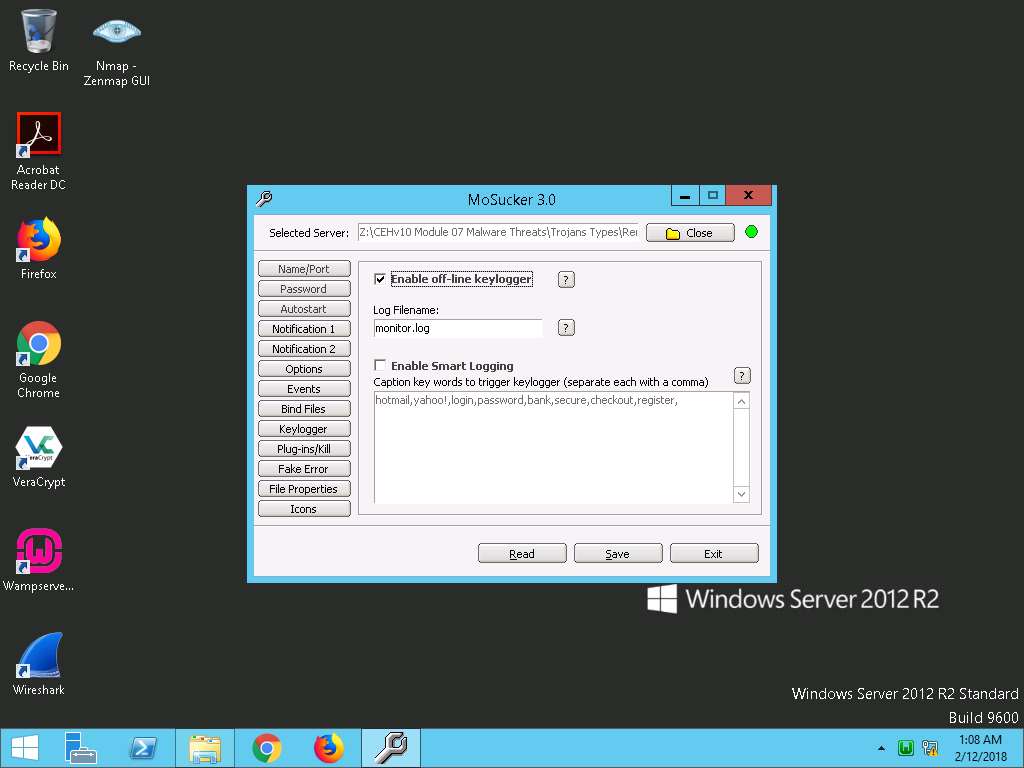
- Once the Trojan server is saved successfully, a MoSucker EditServer pop-up appears; click OK.
Exit the MoSucker Configuration wizard by clicking Exit.
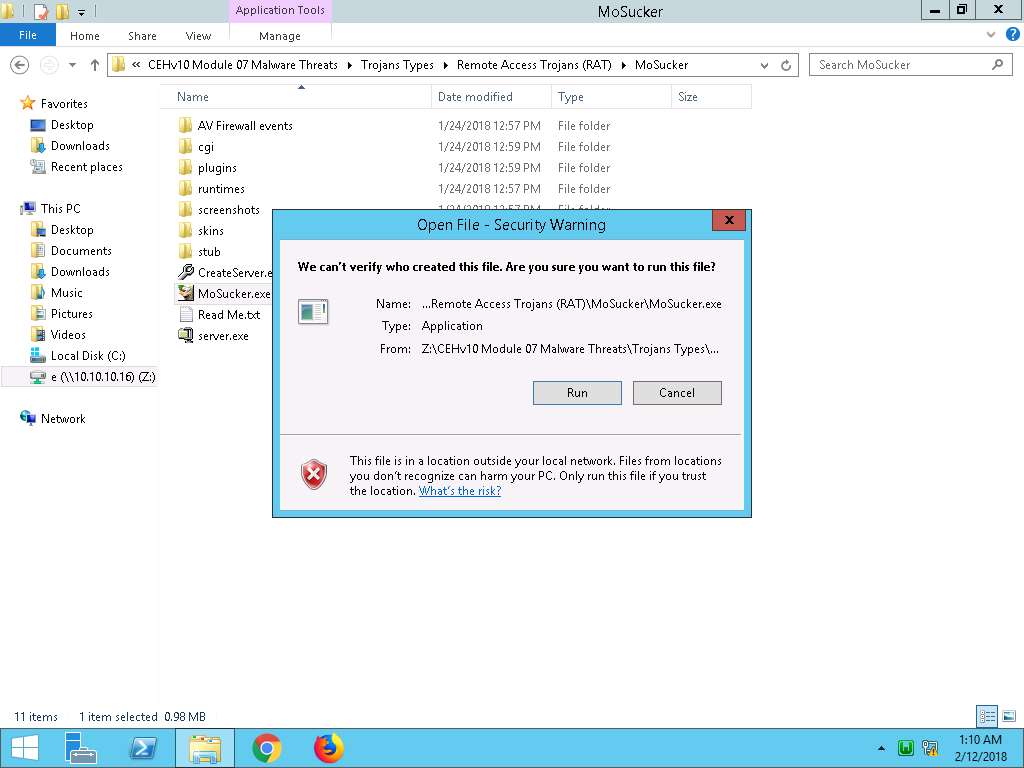
- Now, navigate to Z:\CEHv10 Module 07 Malware Threats\Trojans Types\Remote Access Trojans (RAT)\MoSucker, and double-click MoSucker.exe.
If Open File - Security Warning window appears, click Run.
If VB6 Runtimes pop-up appears click OK.
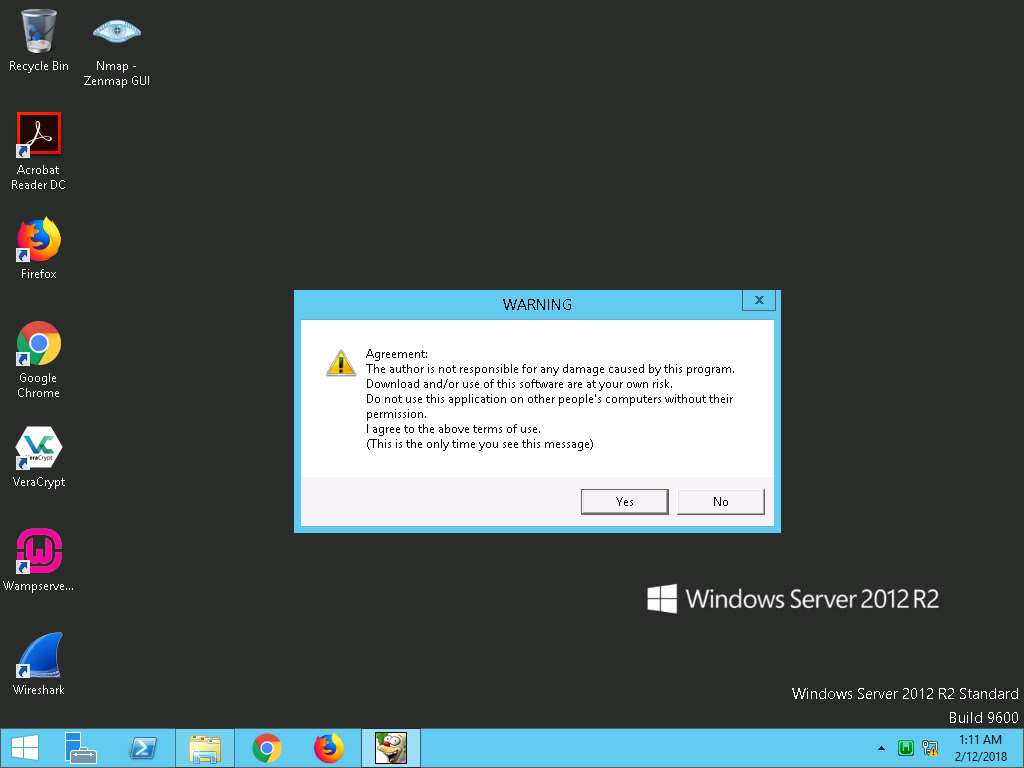
- If Warning pop-up appears, click Yes to continue.
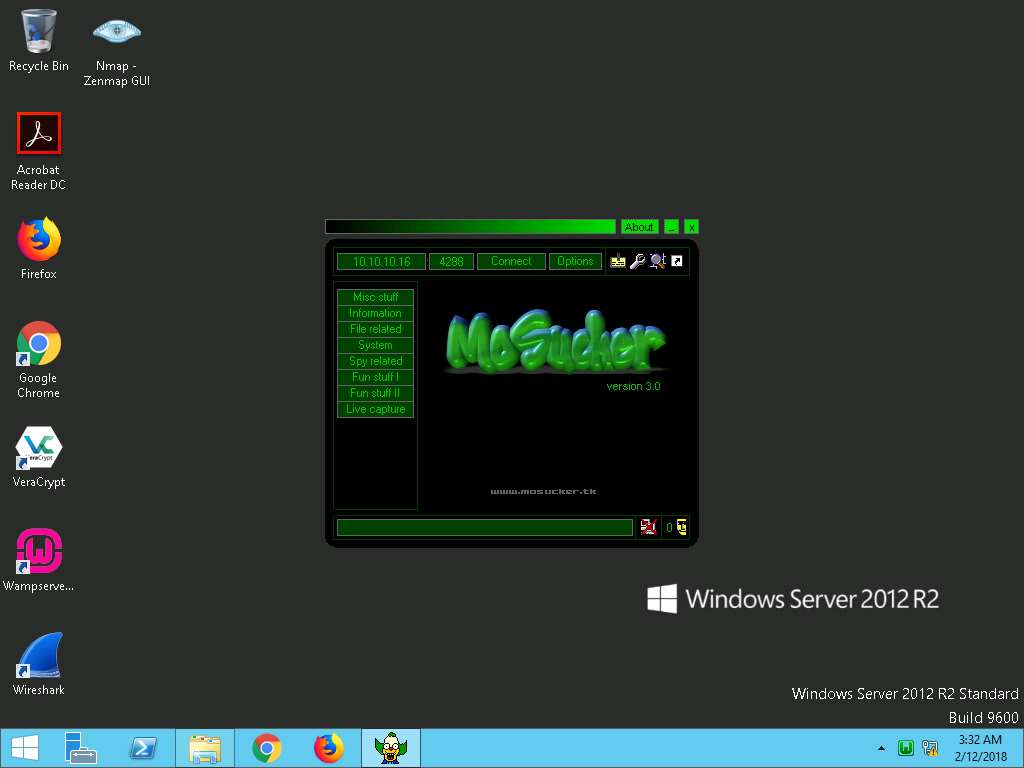
- MoSucker Listener window appears as shown in the screenshot. Now in this lab we are sharing the server.exe file that we have created with the machine Windows Server 2016. Type 10.10.10.16 in the IP address field and 4288 in the Port number field, and leave the MoSucker window running.
In real-time, attackers send a crafted server/backdoor file to the victim, which upon execution on victim machines, allow attackers to view/access all information related to those machines.
- Click Windows Server 2016 pane and click Ctrl+Alt+Delete.
Alternatively navigate to Commands (Thunder icon) menu and click Ctrl+Alt+Delete.
- In the Password field click Pa$$w0rd and press Enter to login.
Alternatively navigate to Commands (Thunder icon) menu Type Text and click Type Password.
- Now, navigate to E:\CEHv10 Module 07 Malware Threats\Trojans Types\Remote Access Trojans (RAT)\MoSucker and double-click server.exe.
- If an administrator error pop-up appears, click OK to close it.
If Program Compatibility Assistant pop-up appears, click Run the program using compatibility settings.
- Click Windows Server 2012, MoSucker window appears, type the IP address of the Windows Server 2016 in the IP Address field, type 4288 in the Port number field, and click Connect.
As soon as you click Connect, the victim machine will get connected to the listener as shown in the screenshot.
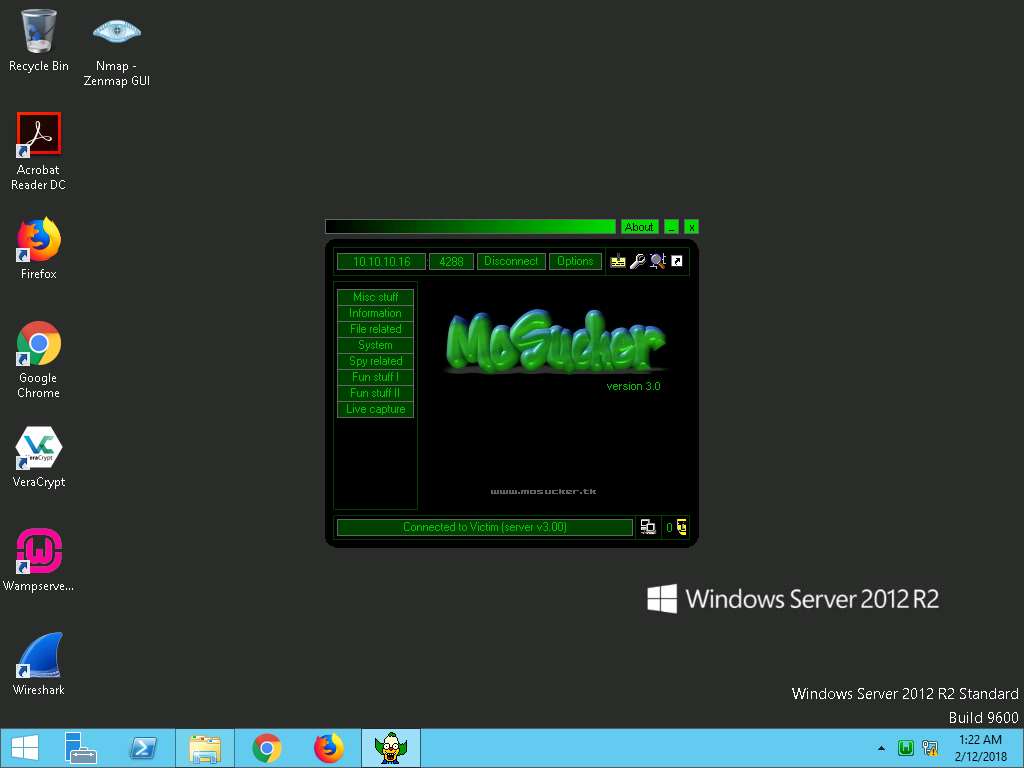
- Now, click on Misc stuff in the left pane. MoSucker displays different options an attacker can use to perform different actions remotely.
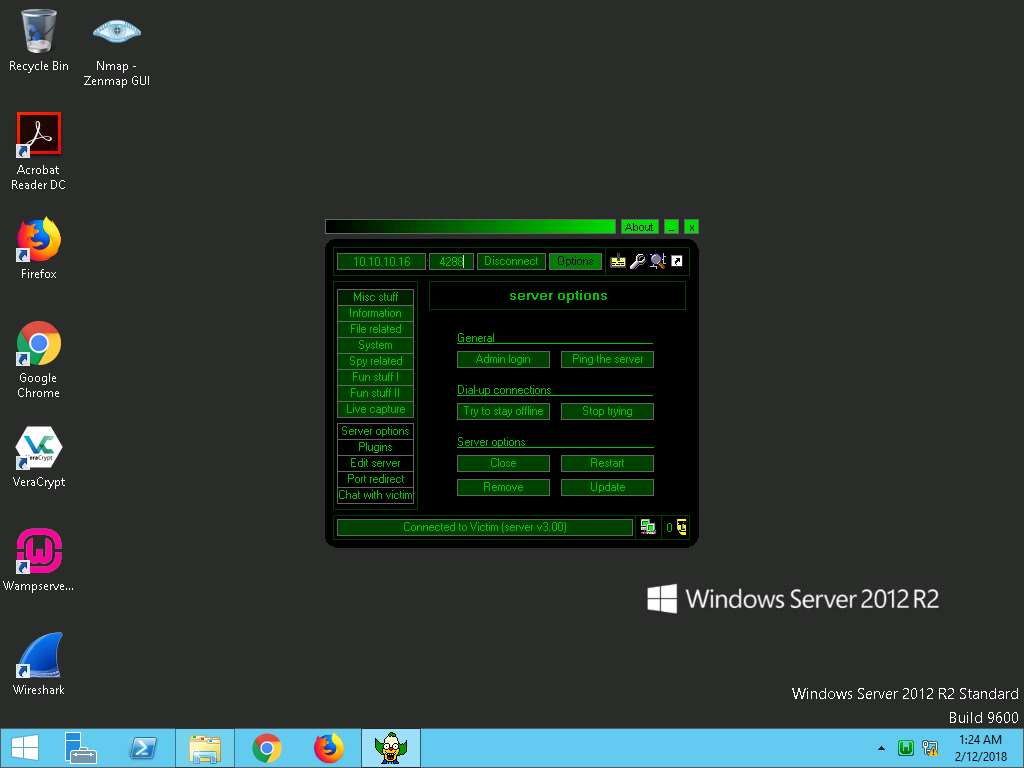
- Click Server options to view different options related to the server. In the same way, you can explore other options that help you perform several other actions on the victim machine.
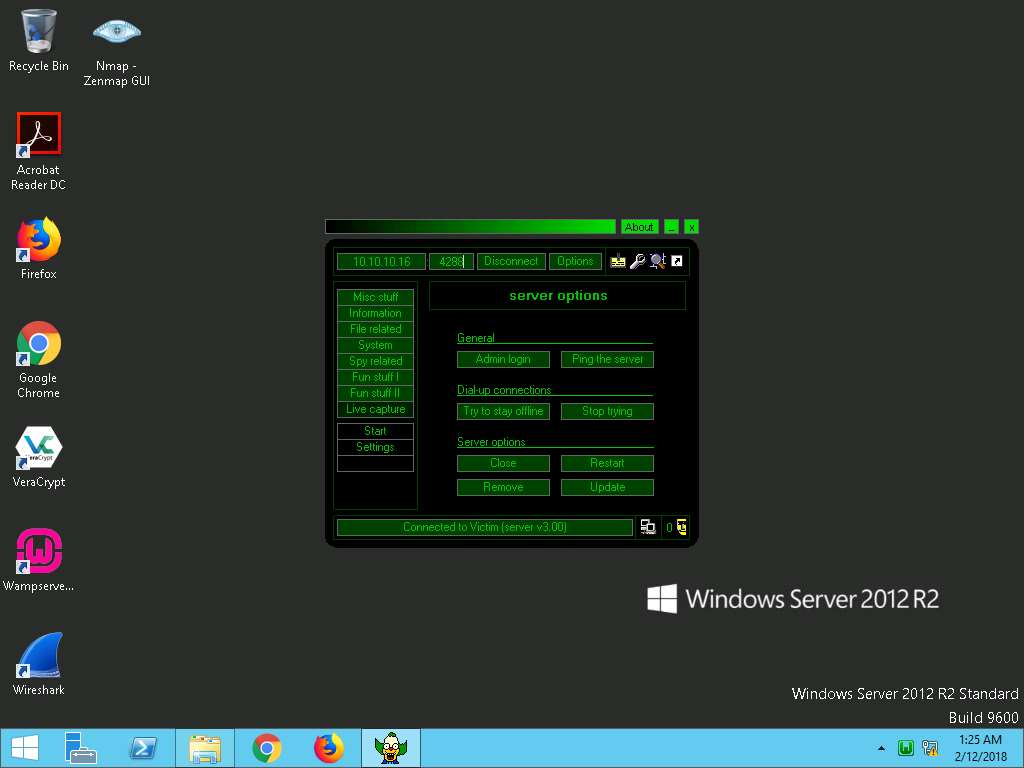
- You can also access the victim machine remotely by clicking Live capture in the left pane. In Live capture, click on Start.
- A DLL missing prompt appears; click Yes to upload the DLL plugin.
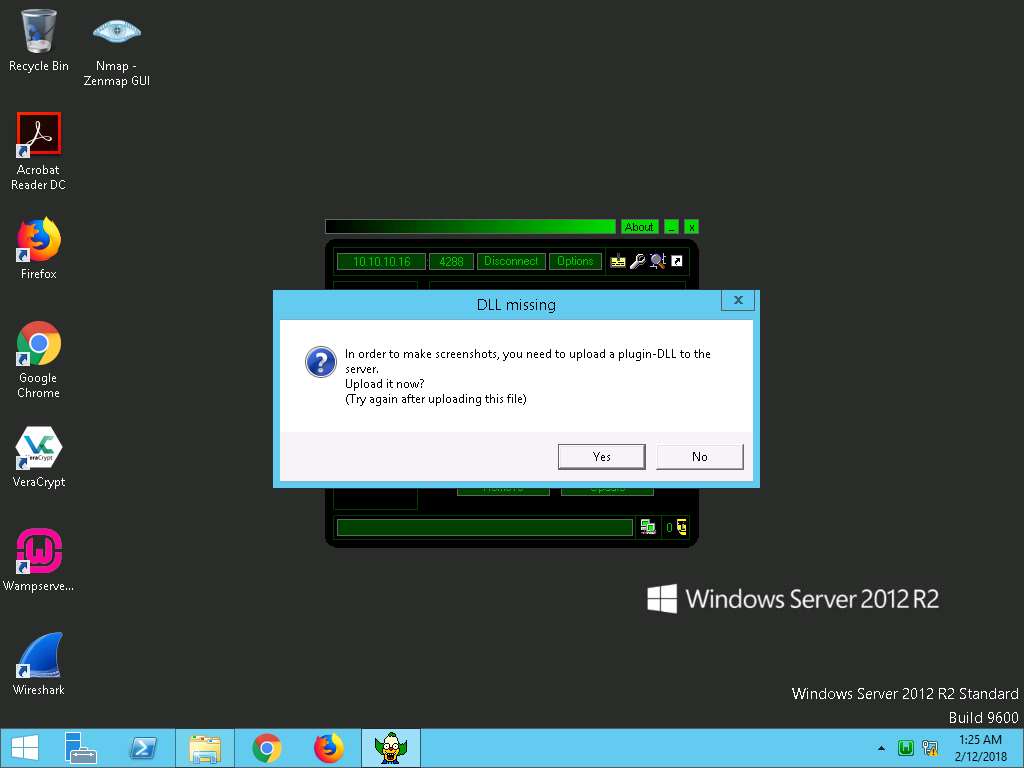
- Click Start again in the MoSucker window if the capture doesn’t begin. You will be able to access the victim machine remotely.
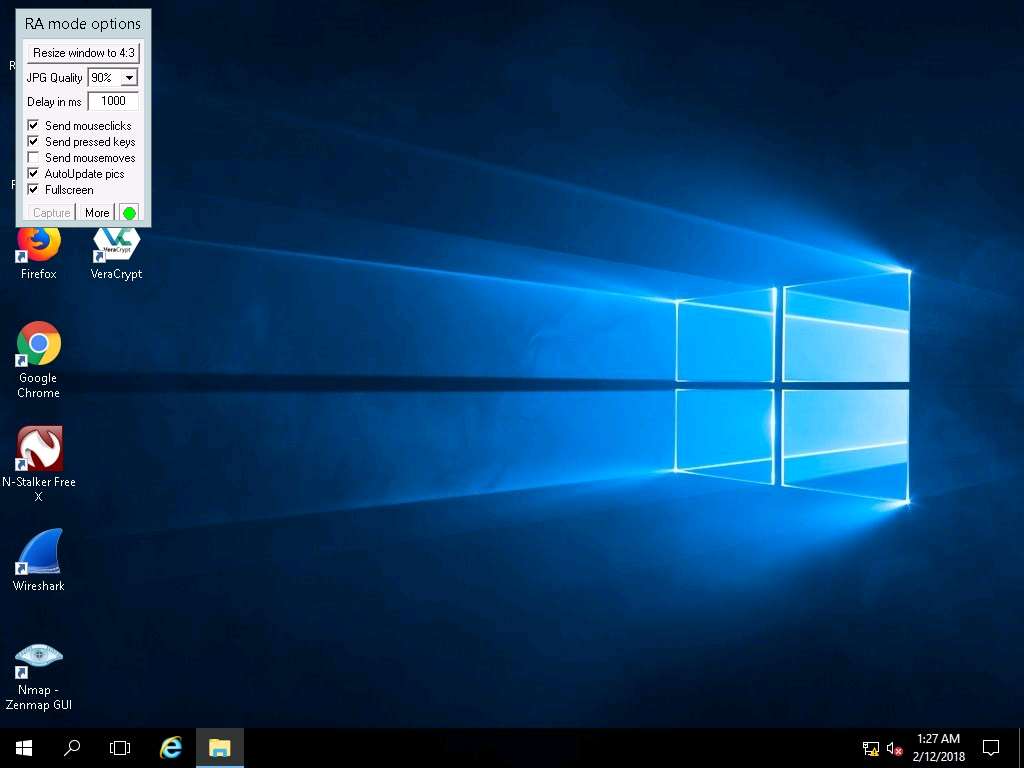
- In the RA mode options, set JPG Quality to 90%, and select Fullscreen. The remote administration mode appears in full screen, as shown in the screenshot.
You can access files, modify them, and so on, in this mode.
Similarly, you can use other functionalities in MoSucker, such as keyloggers, the registry editor, and window manager.
Close the Live Capture window.
- On completion of the lab, close all the windows.
In this lab you have learnt how to:
- Create a server and testing the network for attack
- Access the victim machine remotely
