Exercise 4: Obfuscating a Trojan Using SwayzCryptor and Making it Undetectable to Various Anti-Virus Programs
At present, there have been numerous anti-virus software programs configured to detect malware such as Trojans, viruses and worms. Though security specialists keep updating the virus definitions, hackers try to evade/bypass them by some or the other means. One method which attackers use to bypass AVs is to “crypt” (an abbreviation of “encrypt”) the malicious files using fully undetectable crypters (FUDs). Crypting these files allow them to achieve their objectives and thereby taking complete control over the victim machine.
As an expert security auditor or ethical hacker, you need to ensure that your organization’s network is secure from such encrypted malware files, and anti-virus tools are properly configured to detect and delete such files.
As an expert security auditor or ethical hacker, you need to ensure that your organization’s network is secure from such encrypted malware files, and anti-virus tools are properly configured to detect and delete such files.
Crypter is a software that encrypts the original binary code of the .exe file to hide viruses, spyware, keyloggers, Remote Access Trojans (RATs), among others, to make them undetectable by anti-viruses.
The objective of this lab is to make students learn and understand how to crypt a Trojan and make it partially/completely undetectable.
Lab Duration: 15 Minutes
- Stay in the Windows Server 2016 machine running from the previous lab and do not close the NjRAT window.
Navigate to E:\CEHv10 Module 07 Malware Threats\Crypters\SwayzCryptor and double-click SwayzCryptor.exe to launch the application.
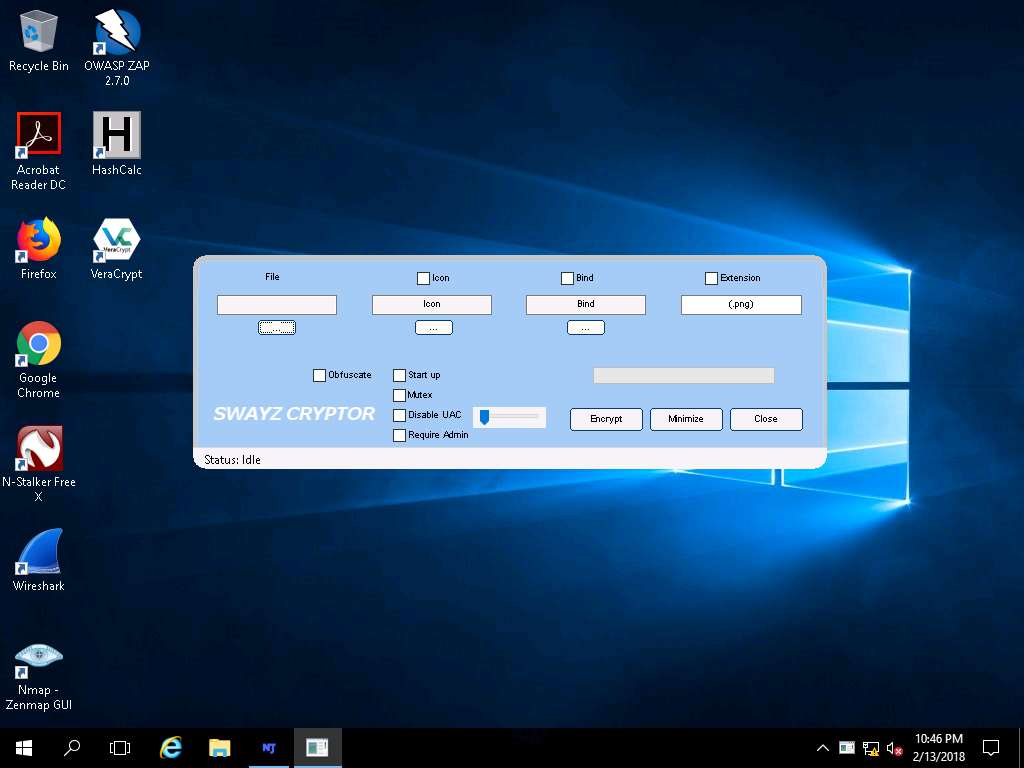
- The application main window appears, click the ellipsis icon on the bottom of File heading.
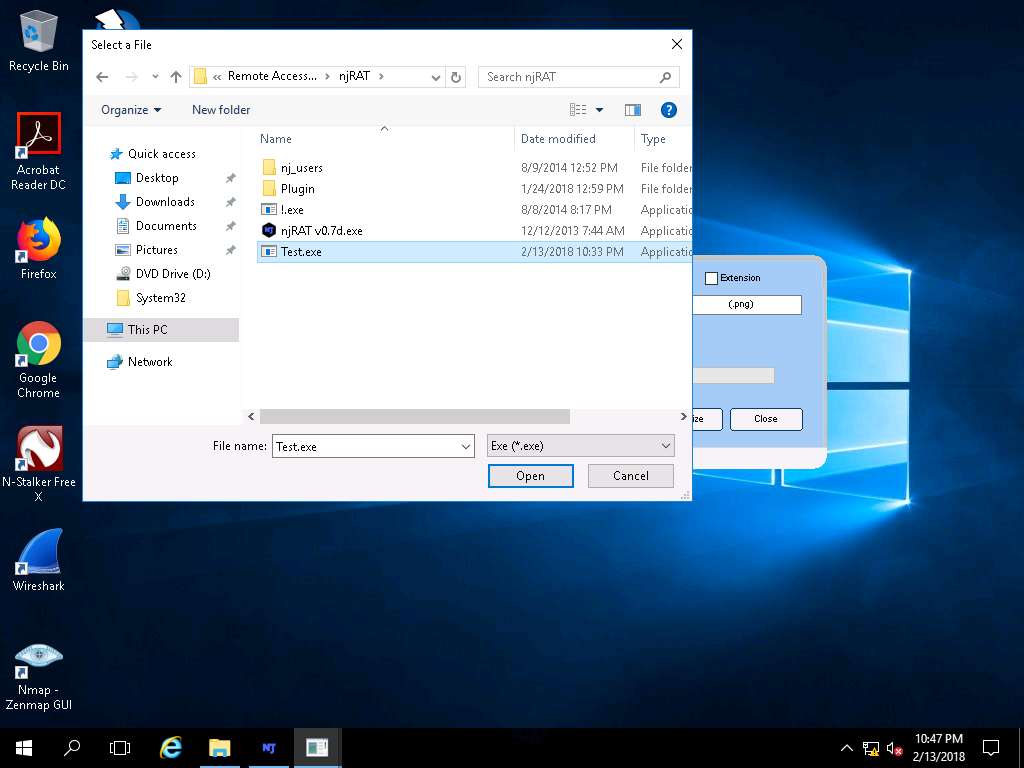
- Select a File window appears, navigate to E:\CEHv10 Module 07 Malware Threats\Trojans Types\Remote Access Trojans (RAT)\njRAT then select Test.exe and click Open.
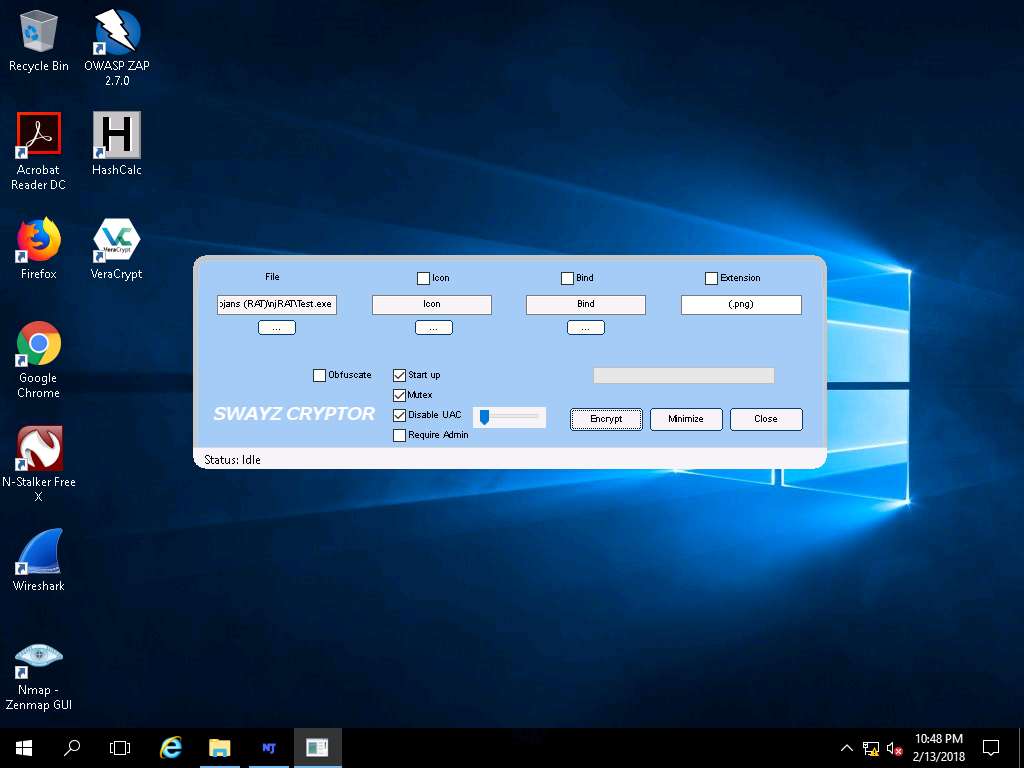
- Once the file is selected, check the options Start up, Mutex, and Disable UAC, and click Encrypt.
- The Save File dialog-box appears; select the save location same as the Test.exe file (E:\CEHv10 Module 07 Malware Threats\Trojans Types\Remote Access Trojans (RAT)\njRAT), leave the file name set to its default (CryptedFile.exe), and click Save.
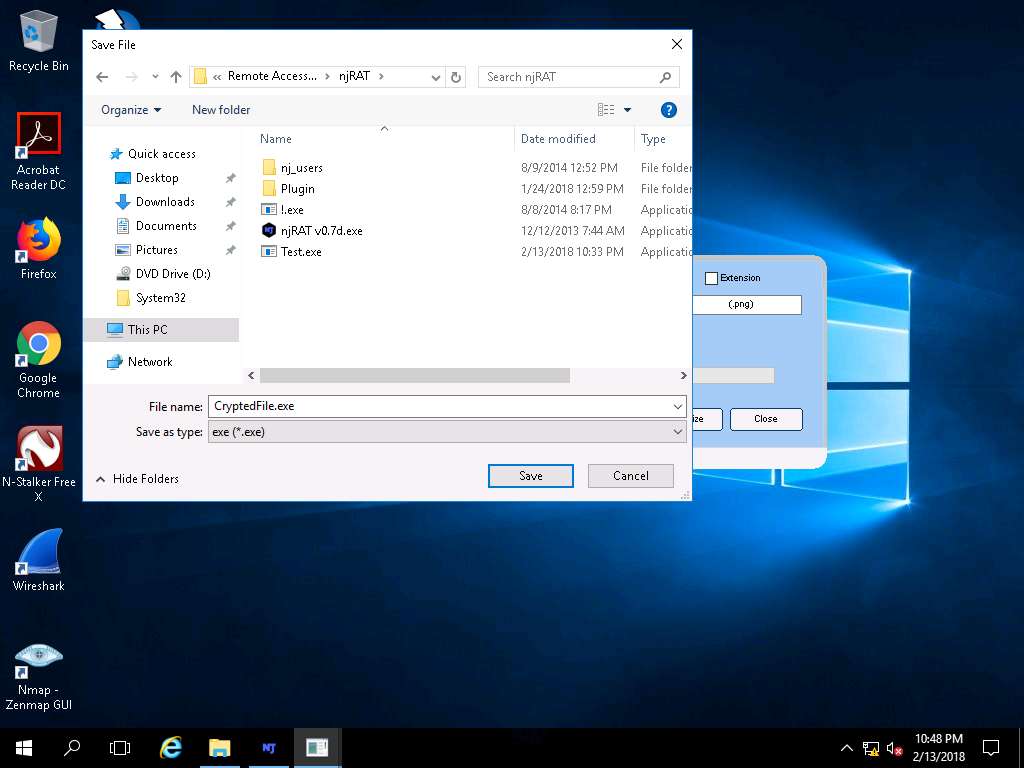
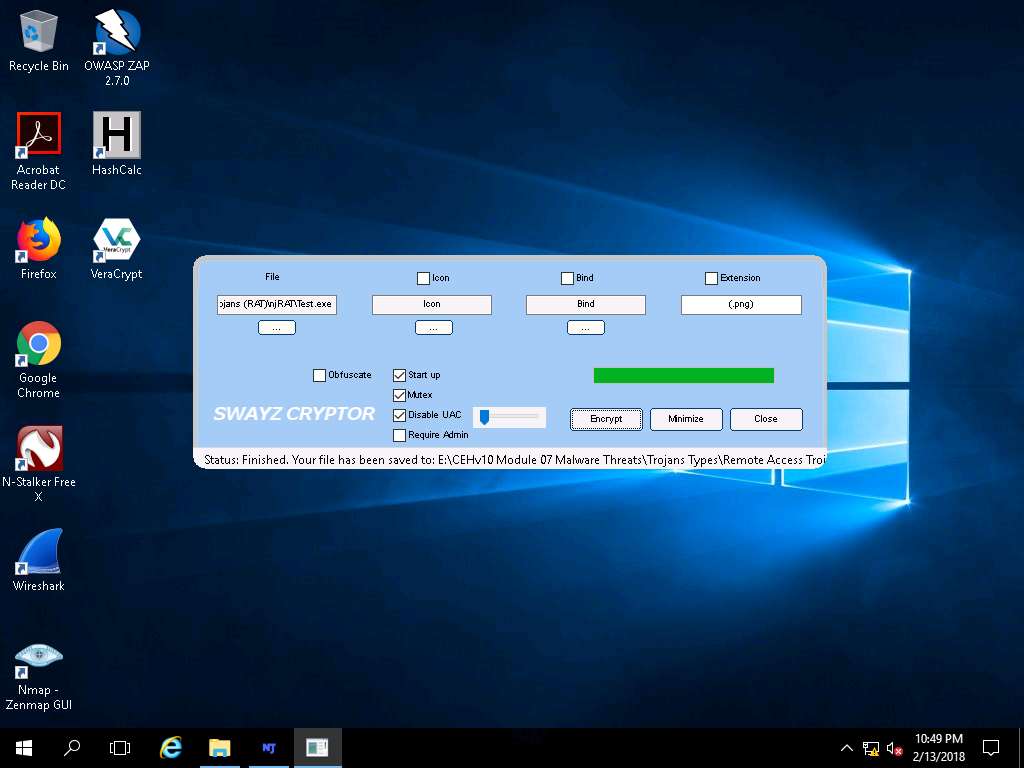
- Once the encryption is finished, click Close.
- Click Windows Server 2012 pane and click Ctrl+Alt+Delete.
Alternatively navigate to Commands (Thunder icon) menu and click Ctrl+Alt+Delete.
- In the Password field click Pa$$w0rd and press Enter to login.
Alternatively navigate to Commands (Thunder icon) menu Type Text and click Type Password.
- Navigate to the location of the CryptedFile.exe (Z:\CEHv10 Module 07 Malware Threats\Trojans Types\Remote Access Trojans (RAT)\njRAT). Copy the CryptedFile.exe and paste it on the Desktop. Double-Click the CryptedFile.exe from the Desktop to run it.
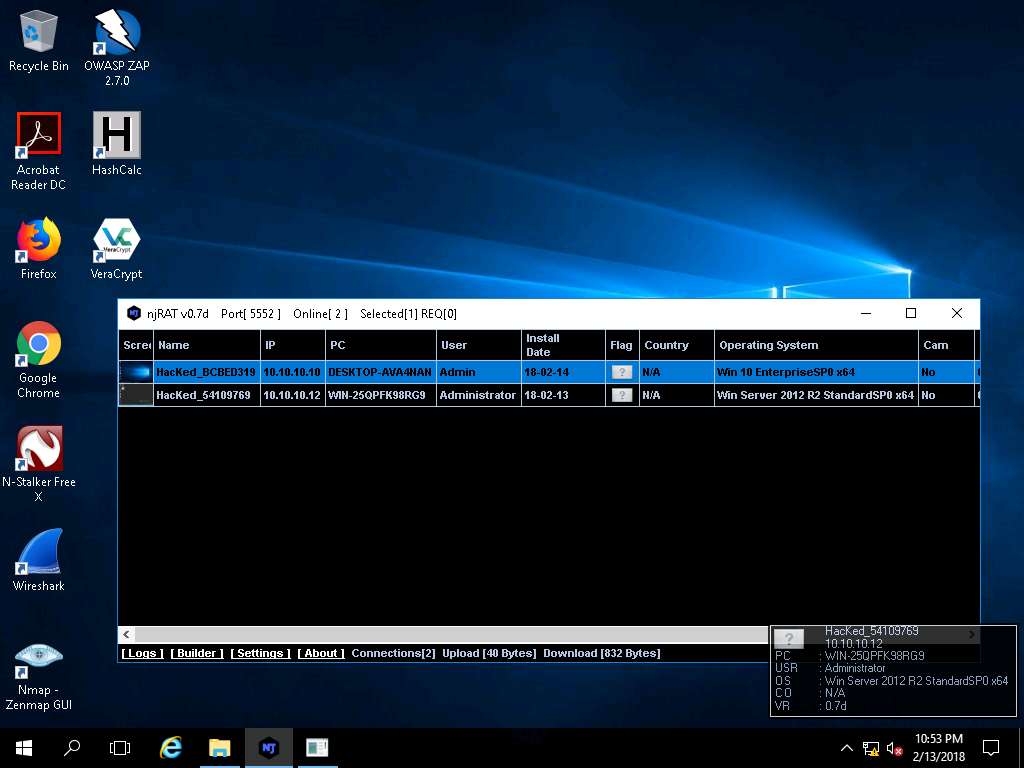
- Click Windows Server 2016, as soon as the victim (here, you) double-clicks the server, the executable starts running and the njRAT client (njRAT GUI) running in Windows Server 2016 establishes a persistent connection with the victim machine as shown in the screenshot.
Unless the attacker working on the Windows Server 2016 machine disconnects the server on his own, the victim machine remains under his/her control.
The GUI displays the machine’s basic details such as the IP address, User name, Type of Operating system and so on.
- Close all the windows which were open after the lab is done..
In this lab you have learned how to encrypt a Trojan and make it partially/completely undetectable.
