Exercise 6: Creating a Trojan Server Using Theef
Theef is a Remote Access Trojan written in Delphi and it allows remote attackers access to the system via port 9871. It is a Windows-based application on both the client and server ends. The Theef server is a virus installed on the victim's system, and using Theef client, an attacker can control the virus.
Lab Scenario
A backdoor is a program which can bypass the standard system authentication or conventional system mechanism like IDS, firewalls, etc. without being detected. In these types of breaches, hackers leverage backdoor programs to access the victim’s computer or a network. This allows the attack to perform any activity on the infected computer which can include transferring, modifying, corrupting files, installing malicious software, rebooting the machine, etc. without user detection. Backdoor Trojans are often used to group victim computers to form a botnet or zombie network that can be used to perform criminal activities.
Lab Objectives
The objective of this lab is to help students learn to detect Trojan and backdoor attacks. The objectives of this lab include:
The objective of this lab is to help students learn to detect Trojan and backdoor attacks. The objectives of this lab include:
- Creating a server and testing the network for attack
- Attacking a network using sample Trojans and documenting all vulnerabilities and flaws detected
Lab Duration: 5 Minutes
- Click Windows Server 2012, and then click Ctrl+Alt+Delete.
Alternatively click Ctrl+Alt+Delete from Commands menu (Thunder icon).
- In the Password field click Pa$$w0rd and press Enter to login.
Alternatively navigate to Commands (Thunder icon) menu Type Text and click Type Password.
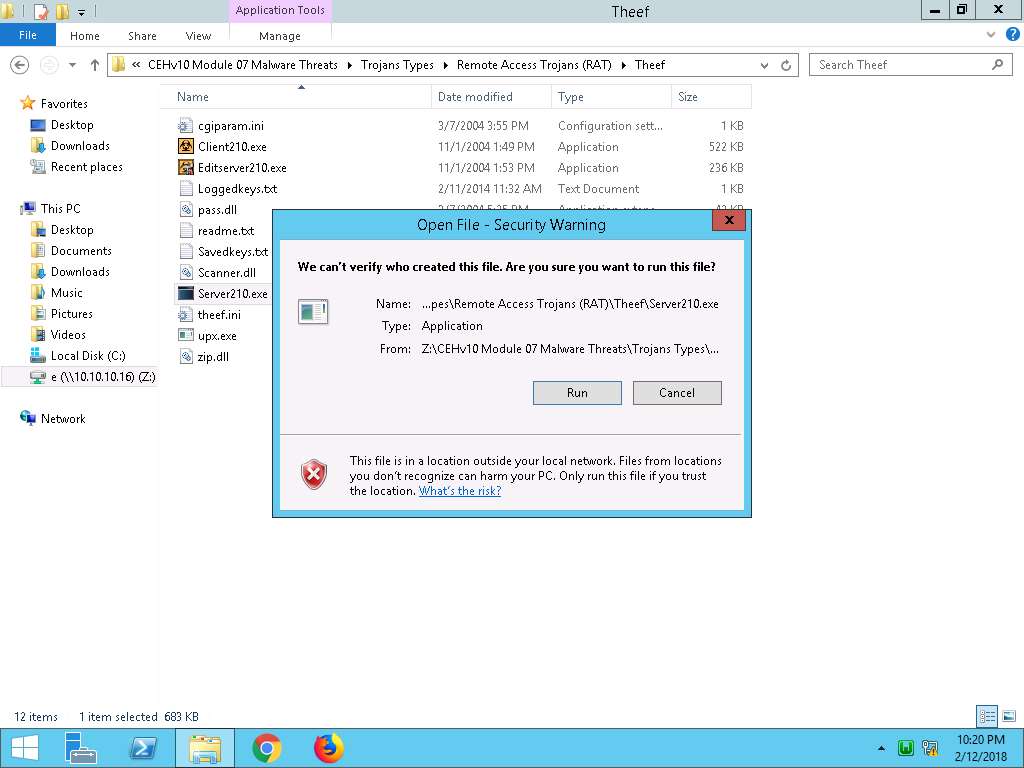
- Generally, an attacker might send a server executable to the victim machine and entice the victim to run it. In this lab, for demonstration purpose, we are directly executing the file in the victim machine, Windows Server 2012.
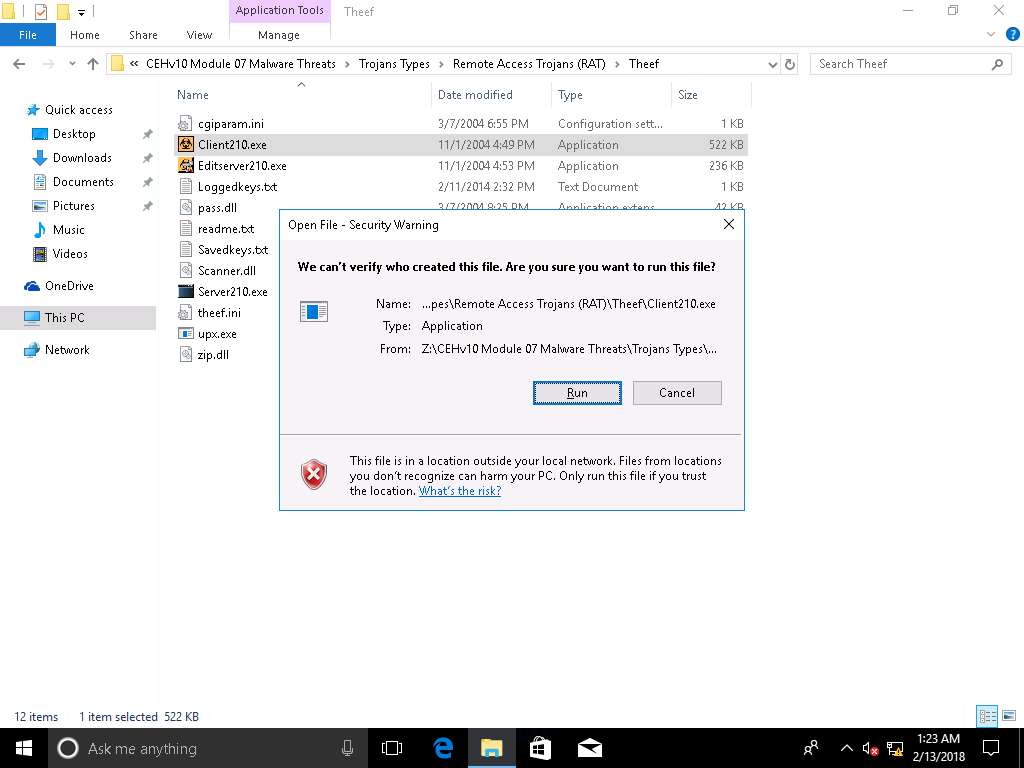
Navigate to Z:\CEHv10 Module 07 Malware Threats\Trojans Types\Remote Access Trojans (RAT)\Theef. Double-click Server210.exe to run the Trojan on the victim’s machine. If the Open File - Security Warning pop-up appears, click Run.
- Click Windows 10, and then click Ctrl+Alt+Delete.
Alternatively click Ctrl+Alt+Delete from Commands menu (Thunder icon).
- In the Password field click Pa$$w0rd and press Enter to login.
Alternatively navigate to Commands (Thunder icon) menu Type Text and click Type Password.
- Navigate to Z:\CEHv10 Module 07 Malware Threats\Trojans Types\Remote Access Trojans (RAT)\Theef, and double-click Client210.exe to access the victim machine remotely.
If the Open File - Security Warning pop-up appears, click Run.
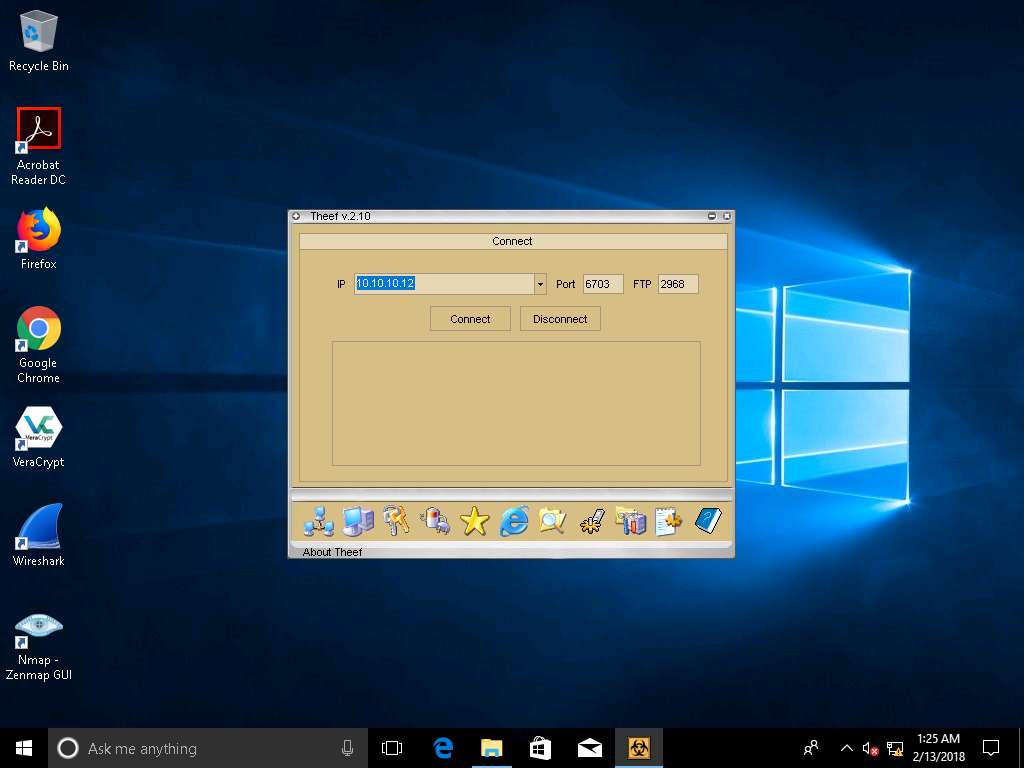
- The main window of Theef appears as shown in the screenshot, enter the target (Windows Server 2012) IP Address in the IP field (10.10.10.12), and leave the Port and FTP fields set to default. Click Connect.
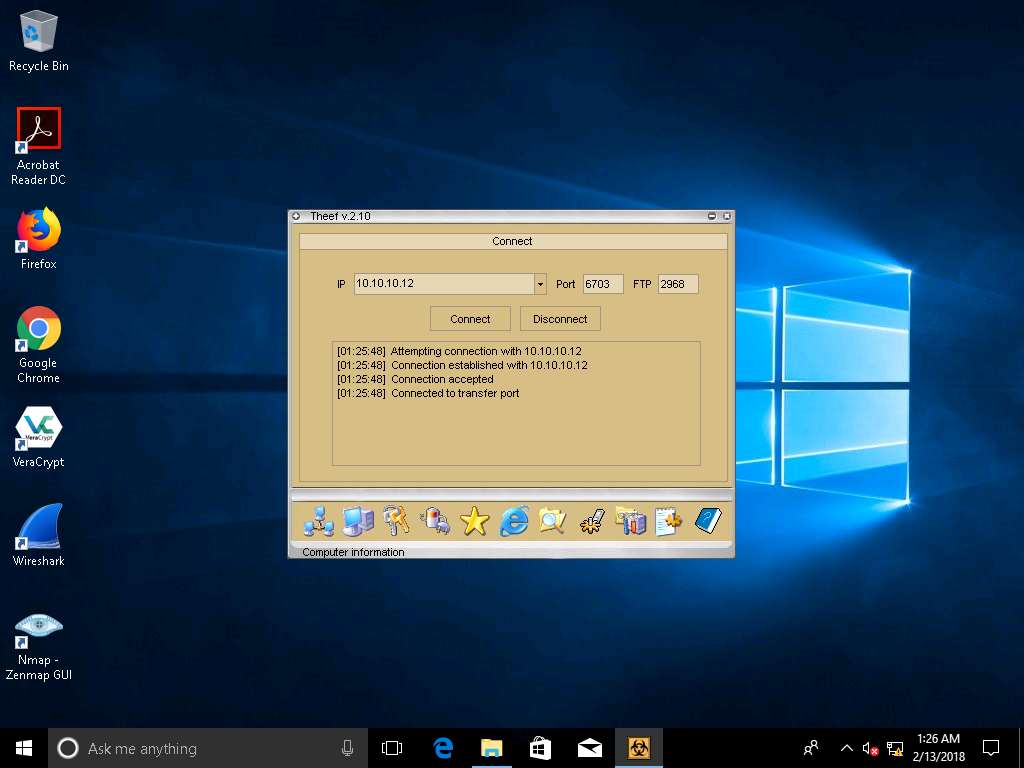
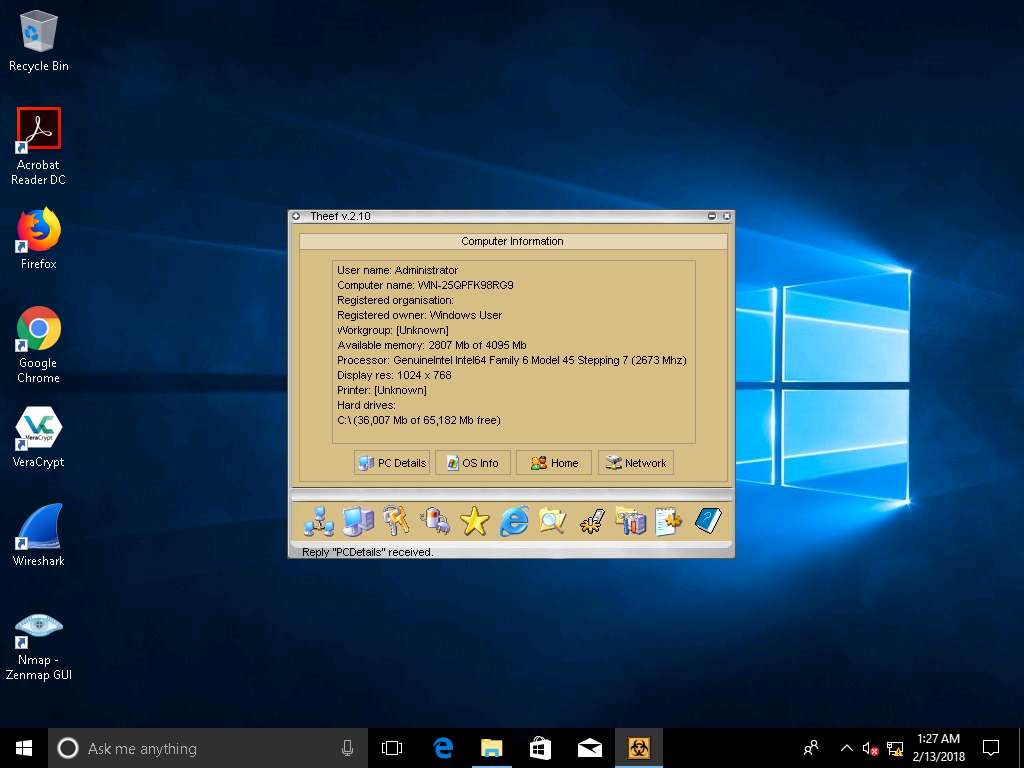
- Now, in Windows 10 you have successfully established a remote connection with Windows Server 2012. To view the Computer Information, click on Computer Information in the lower part of the window.
- In Computer Information, you can view PC Details, OS Info, Home, and Network by clicking their respective buttons. Here, for instance, PC Details has been selected to view computer-related information.
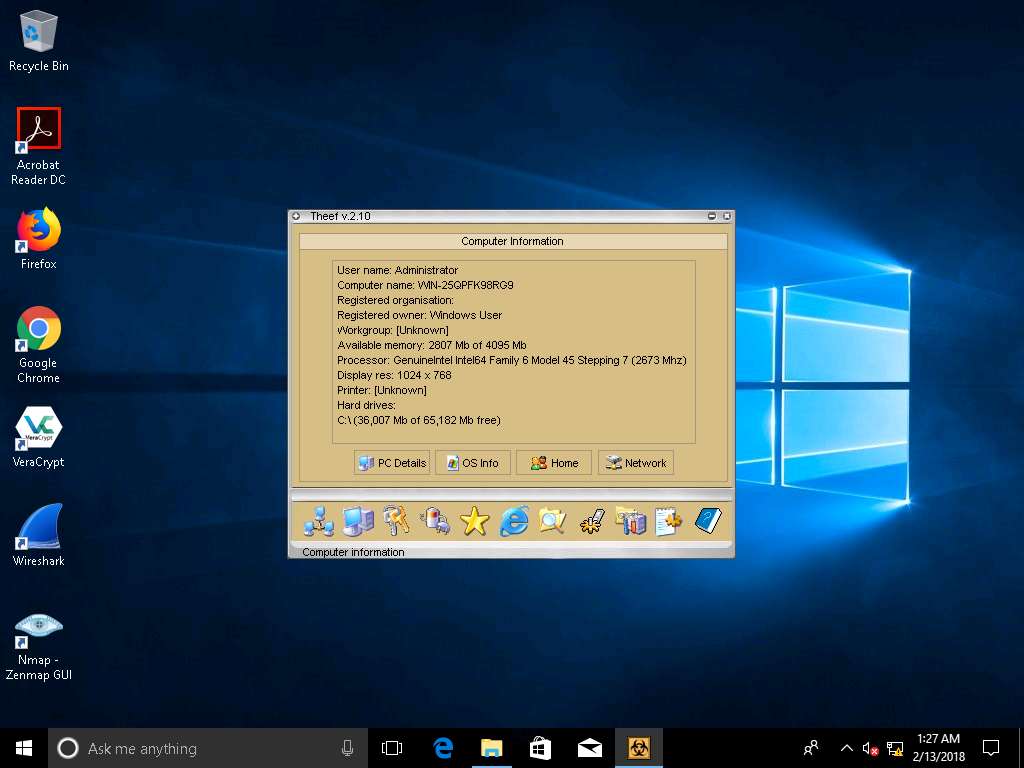
- Click Spy (Keys Icon) to capture screens, Keyloggers, etc. of the victim machine.
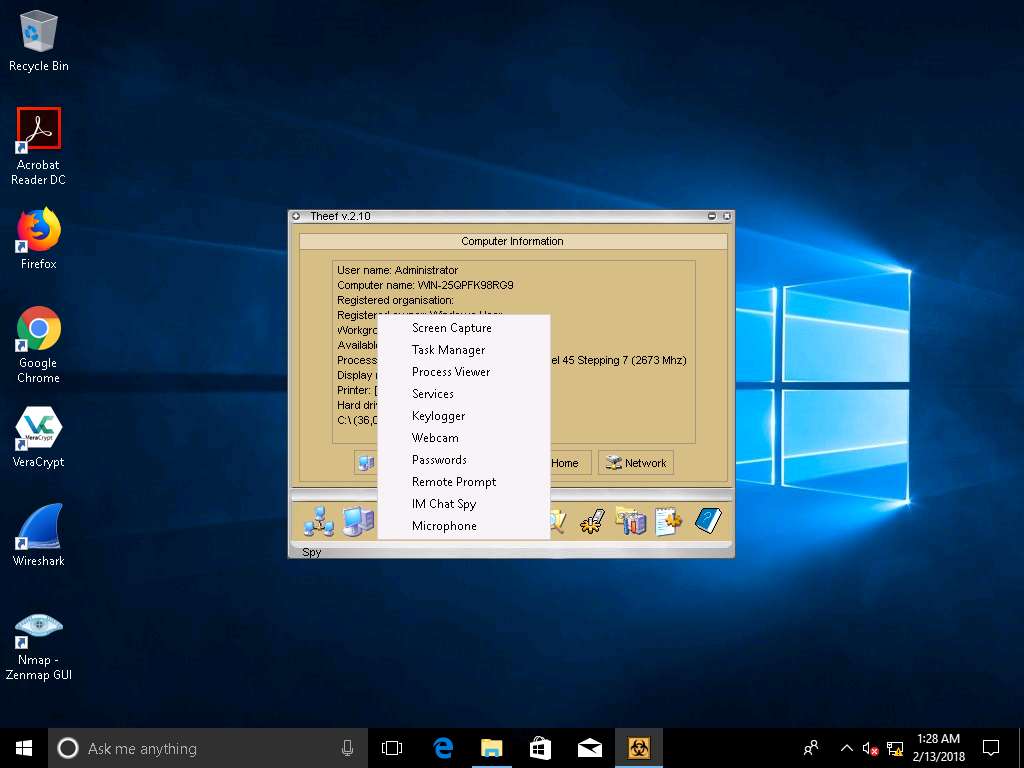
- Select Task Manager to view the tasks running on the target machine.
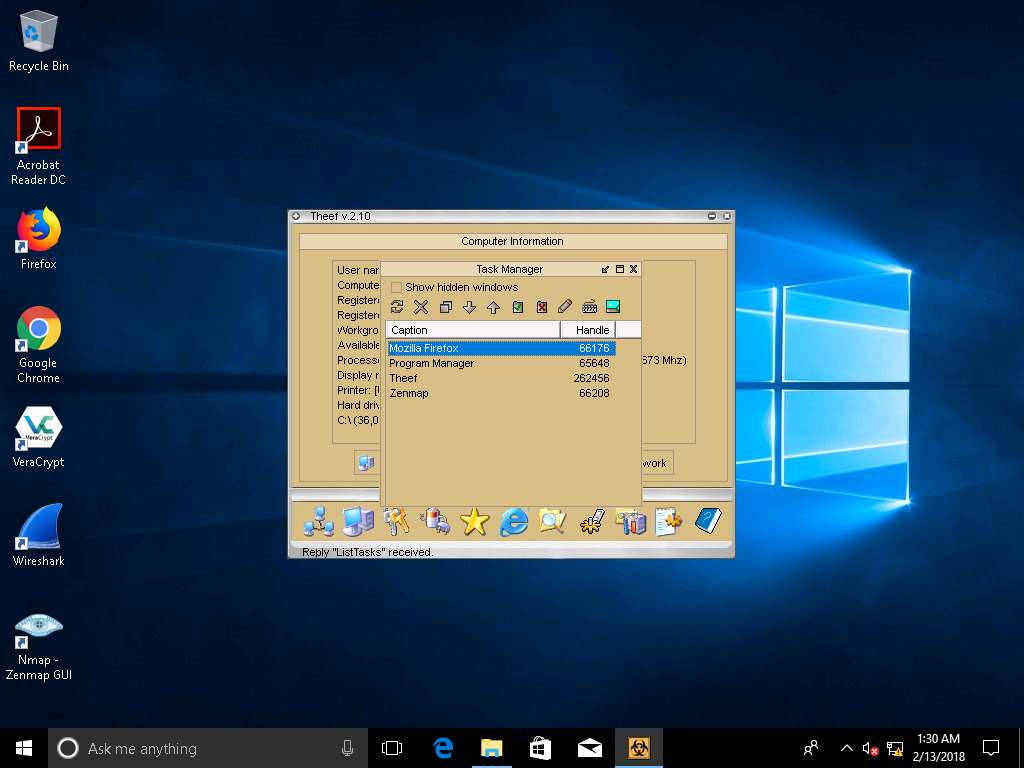
- In the Task Manager window, select a process (task), and click Close window to end the task in the target machine. Similarly, you can access the details of the victim machine by clicking on respective icons.
- On completion of the lab, close all the windows.
In this lab you have learnt how to:
- Creating a server and testing the network for attack
- Attacking a network using sample Trojans and documenting all vulnerabilities and flaws detected
